How easy is it to capture data on public free Wi-Fi
Page 1 of 1
 How easy is it to capture data on public free Wi-Fi
How easy is it to capture data on public free Wi-Fi
androidauthority.com/capture-data-open-wi-fi-726356/
How easy is it to capture data on public free Wi-Fi? – Gary explains
Features
by Gary SimsFebruary 14, 2018
If you have read my article on what is a VPN? or read my review of Express VPN, you will have noticed that I recommend a level of caution when connecting to free public Wi-Fi hotspots. The reason is that all the traffic that goes from your device to the Wi-Fi router is unencrypted and because it is unencrypted then anyone who is within range of the same Wi-Fi signal can look at your Internet traffic! So, here is the question, just how easy is it to steal data on public free Wi-Fi?
There are three main problems with unencrypted public Wi-Fi hotspots. First, as I have mentioned, the packets of data that go from your device to the router are public and open for anyone to read. That sounds scary and it is, but thankfully because of tech like SSL/TLS it isn’t as bad as it was a few years ago.
Editor's Pick
Second, hackers can quickly create fake rogue Wi-Fi hotspots, setup just to steal your info. Have you ever said to yourself, “Great! The coffee shop now has free Wi-Fi, it didn’t last week, they must have upgraded.” Did the coffee shop upgrade? Or is it some hacker just setting up a honey pot to catch you unawares?
Third, public Wi-Fi hotspots can be manipulate to launch man-in-the-middle (MitM) attacks where someone alters key parts of the network traffic or redirects your traffic to the wrong place. You might think you are connecting to Amazon.com but actually you are connecting to the hackers fake server designed just to capture your username and password.

When you want to read a page on a website then your device will make a connection to the webserver to ask for the web page. It does that using a protocol called the HyperText Transfer Protocol (HTTP). On an open Wi-Fi router these requests and the responses can be seen by anyone who is listening. With wired networking then listening to the data packets zipping back and forth is more intrusive. However with wireless networking all that data is sent whizzing through the air, in every direction, for any Wi-Fi equipment to receive!
Normally a Wi-Fi adapter is set into “managed” mode which means it just acts as a client and connects to a single Wi-Fi router for access to the Internet. However, some Wi-Fi adapters can be set into other modes. For example, if I was configuring an access point (a hotspot) then the Wi-Fi needs to be set into “master” mode, more about that soon. Another mode is “monitor” mode. In “managed” mode a Wi-Fi network interface ignores all data packets except those specifically addressed to it. However in “monitor” mode the Wi-Fi adapter will capture all the wireless network traffic (on a certain Wi-Fi channel) regardless of the destination. In fact, in “monitor” mode the Wi-fi interface can capture packets without even being connected to any access point (router), it is a free agent, sniffing and snooping at all the data in the air!
Not all off-the-shelf Wi-Fi adapters can do this as it is cheaper for the manufacturers to make Wi-Fi chipsets that only handle “managed” mode, however there are some out there that can be placed into “monitor” mode. During my testing and research for this article I used the TP-Link TL-WN722N.
The easiest way to sniff Wi-Fi packets is to use a Linux distribution called Kali. You can also use the more standard distributions like Ubuntu, but you will need to install some of the tools yourself. If you don’t have Linux on a laptop then the good news is that Kali Linux can be used on a virtual machine like Virtual Box.
To capture the traffic we are going to use the aircrack-ng suite of tools, plus some others like driftnet, Wireshark and urlsnarf. There are plenty of tutorials out there about capturing traffic with aircrack-ng but here is the essence:
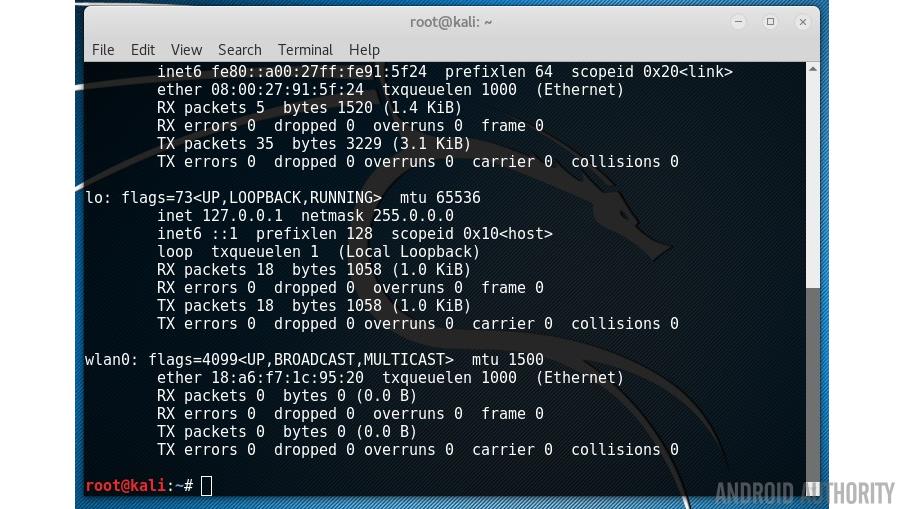
First you need to find out the name of your wireless network adapter, it will probably be wlan0, but to check it run ifconfig and then to double check, run iwconfig:
Next put the card into “monitor” mode, as I mentioned before, not all adapters/cards support this, so you must make sure you are using a compatible adapter. The command is:
sqlSelect All
airmon-ng start wlan0
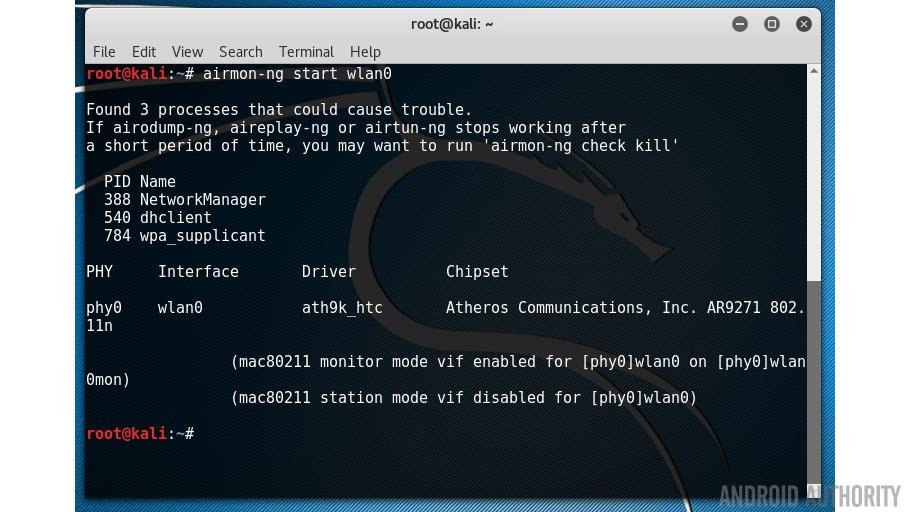
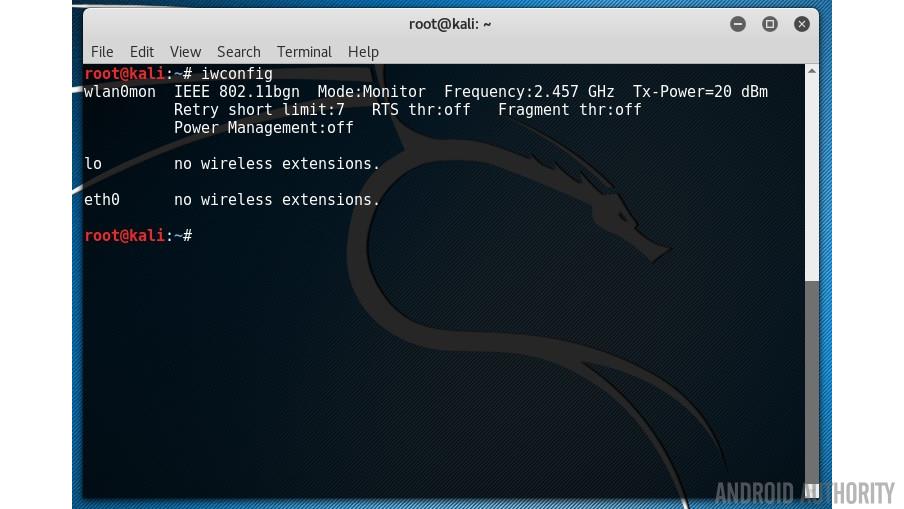
This will create a new virtual interface called wlan0mon (or maybe mon0). You can see it using the iwconfig:
Wi-Fi uses radio and like any radio it needs to be set to a certain frequency. Wi-Fi uses 2.4GHz and 5GHz (depending on which variation you are using). The 2.4GHz range is split into a number of “channels” which are 5MHz apart. To get two channels which don’t overlap at all they need to be spaced around 22MHz apart (but that also depends on which variation of the Wi-Fi standard is being used). That is why channels 1, 6 and 11 are the most common channels as they are far enough apart so that they don’t overlap.
To capture data via a Wi-Fi adapter in “monitor” mode you need to tell the adapter which frequency to tune into, i.e. which channel to use. To see which channels are in use around you and which channel is being used by the free public Wi-Fi service you wish to test then use the airodump-ng command:
Select All
airodump-ng wlan0mon
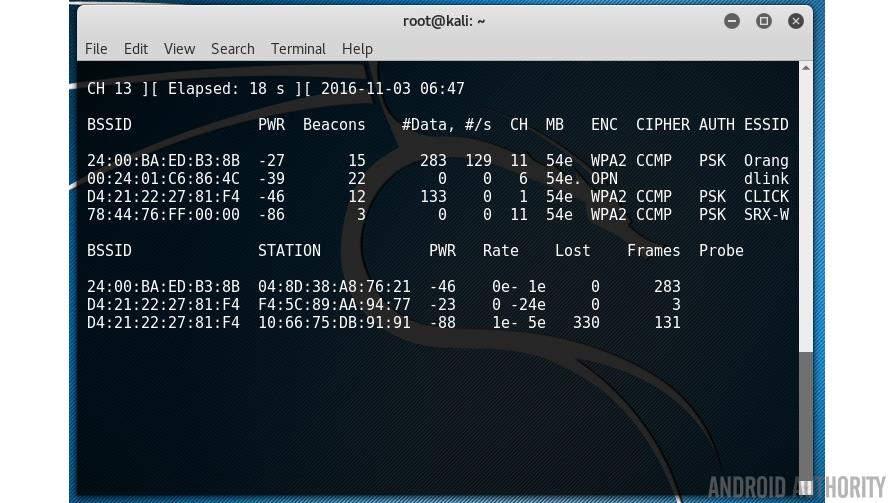
The first list shows the Wi-Fi networks within reach of your laptop. The “CH” tells you which channel number each network is using (11, 6, 1 and 11) and the “ESSID” shows the names of the networks (i.e. the service set identifiers). The “ENC” column reveals if the network is using encryption and if so, what type of encryption. You can see from the screenshot that one of the networks is listed as OPN (i.e. OPEN). This is an open Wi-Fi access point I have setup in my house for testing purposes.
If the free Wi-Fi is on channel 6 then you now use the airodump-ng command to capture the data like this:
Select All
airodump-ng -c 6 -w allthedata wlan0mon
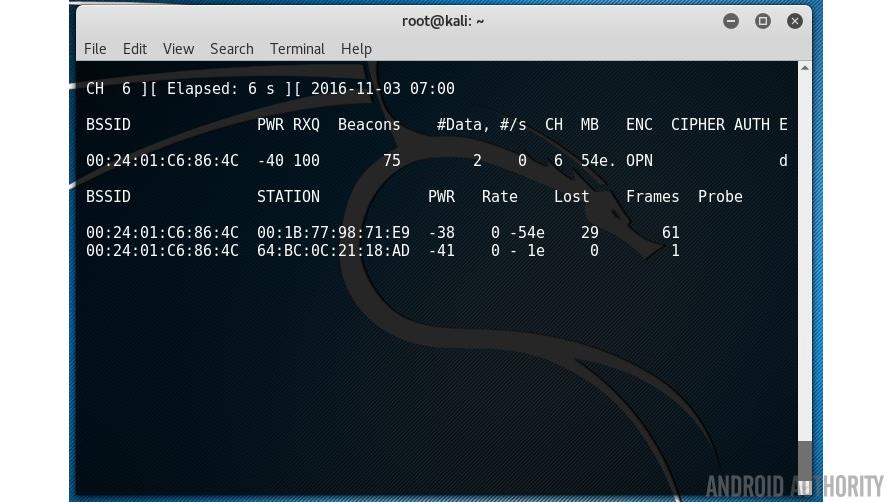
This will start capturing all the data on channel 6 and write it to a file called allthedata-01.cap. Let that run for however long you need and the press CTRL-C to exit.
OK, now we have a big lump of network traffic. The next step is to analyze that data. Network traffic contains lots of different information. For example there are all the broadcast packets which contain the information about the wireless network, the SSID etc. That is what your device receives when it is looking for the available networks. The question is, how can we sort through all the packets and find something interesting.
Each service on the Internet uses what is called a port, this is a way for a service (like a web server) and a client to communicate. Web servers use port 80, Email servers use port 25 (and some others), FTP uses port 21, SSH uses port 22 and so on. A single server can run multiple services (web, email, FTP, etc.) even though the IP address is the same, because each service uses a different port.
What this means is that I can sort the packets by port. I can filter out and examine the traffic working off port 80, i.e all web traffic. Or all the email traffic or whatever. It is also possible to dive deeper into the HTTP traffic and see what kind of data is coming back, images, javascript, whatever.
There are lots of different tools that you can use to filter the data in the network capture. Some simple command line tools include urlsnarf, dsniff and driftnet.
To filter out all the URLs from the data capture use:
Select All
urlsnarf -p allthedata-01.cap
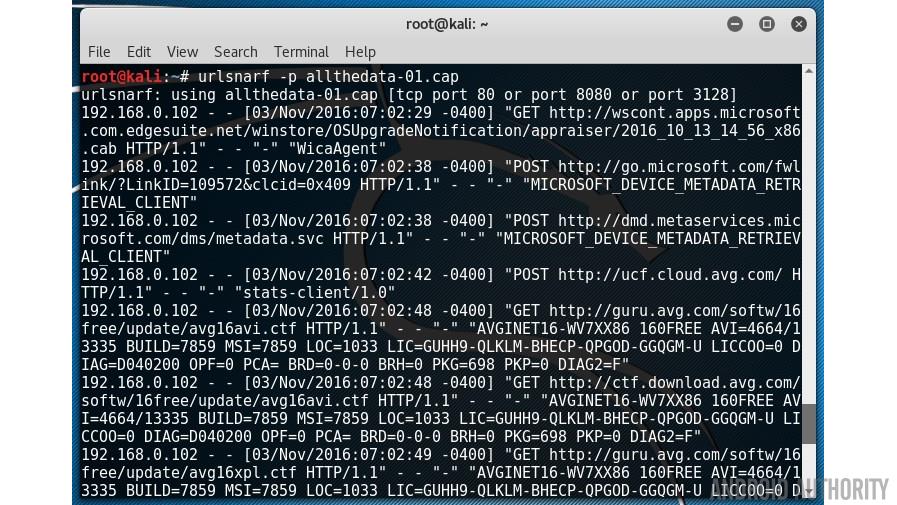
To see if there are any passwords lurking around in the data then use:
Select All
dsniff -p allthedata-01.cap
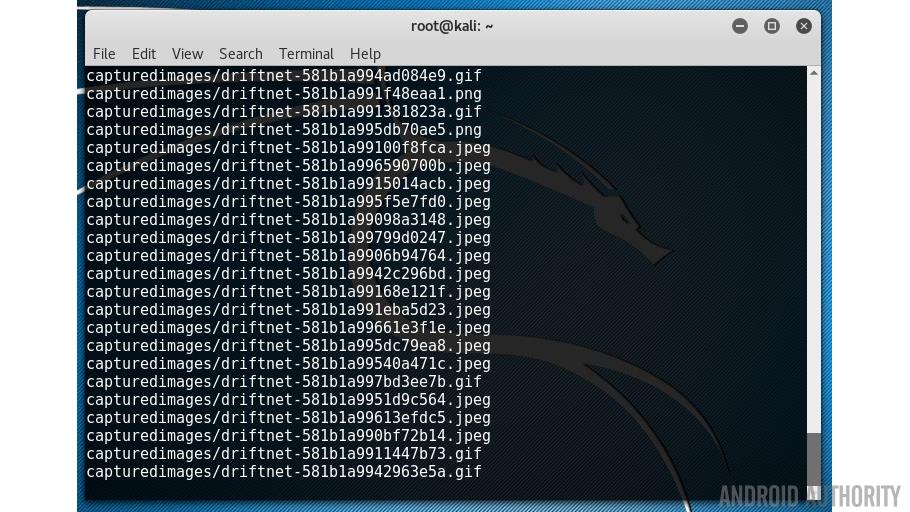
And to see what pictures where being viewed use the driftnet tool:
Select All
driftnet -f allthedata-01.cap -a -d capturedimages
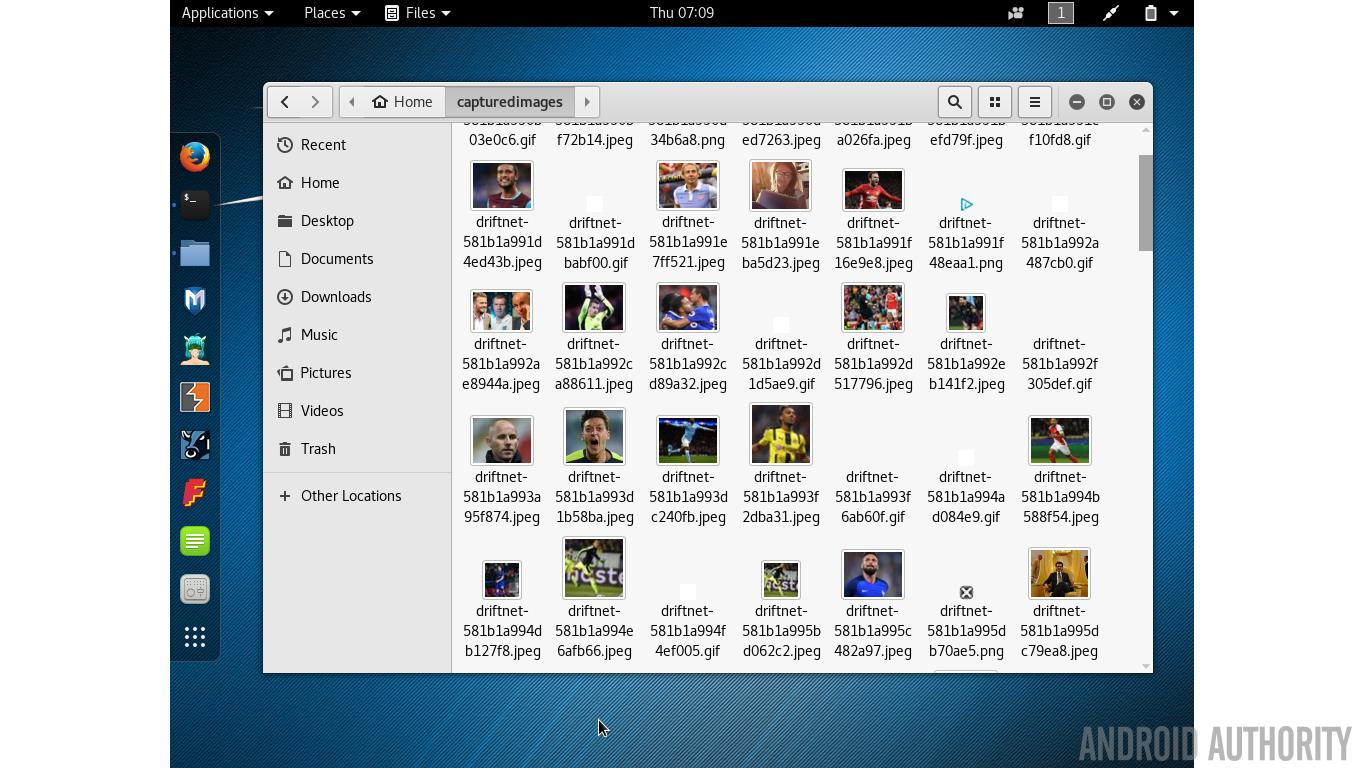
The -a option tells driftnet to write the images to disk rather than display them on screen. The -d option specifies the output directory.
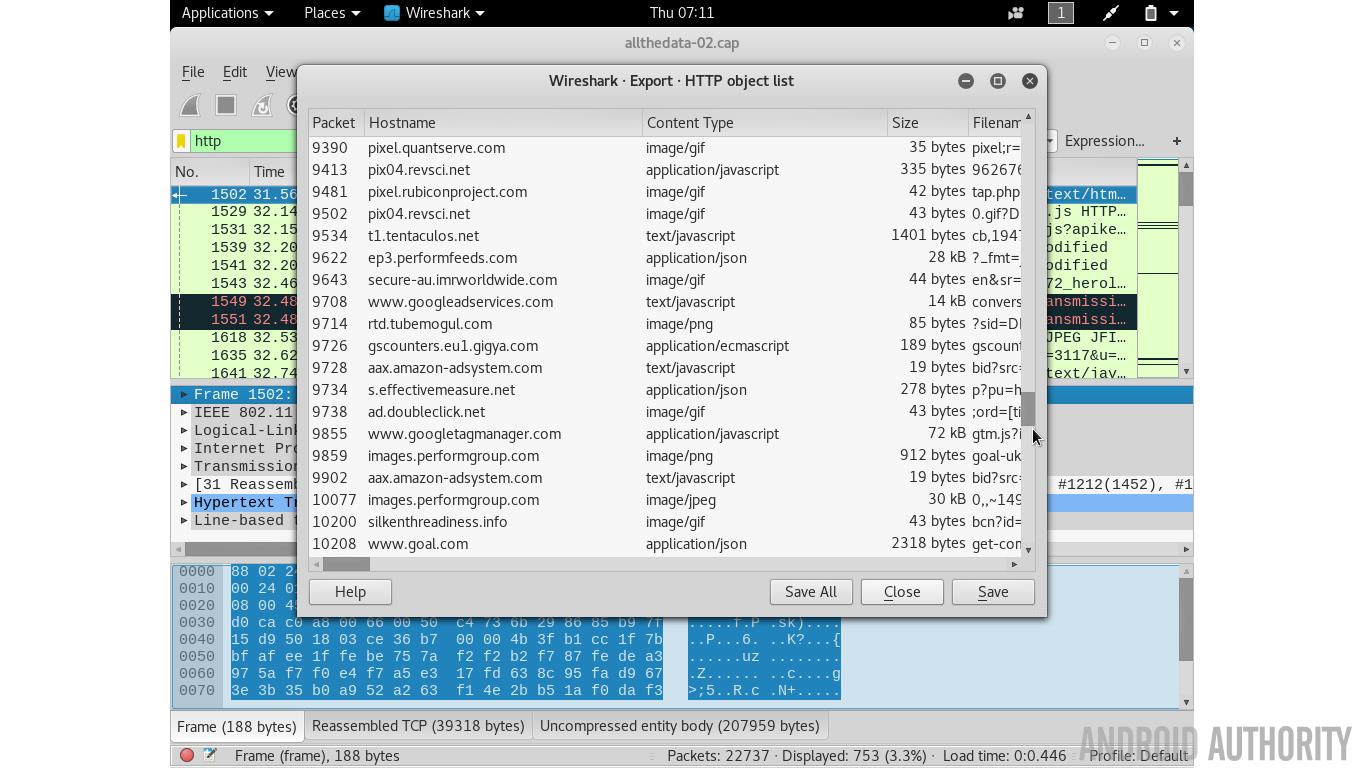
If you don’t like the command line you can use Wireshark. This graphical tool allows you to look at each packet of data individually but it also offers lots of neat filtering. So if you type “http” into the filter bar then only the web related fields will be displayed. There is also the option to export all the images from the HTTP traffic via the File->Export Objects->HTTP menu item.
If this was the end of the story then we would be in a very bad place. Any time you connect to an open Wi-Fi router then you are completely exposed. Thankfully there is help at hand in the form of SSL/TLS. Along side HTTP we have HTTPS, where the extra “S” on the end means secure, i.e. an encrypted connection. In the past HTTPS used SSL (Secure Sockets Layer) but that has now been replaced by TLS (Transport Layer Security). However since TLS 1.0 used SSL 3.0 as its basis then you often find that the two terms are used interchangeably. What TLS and SSL do is provide the protocol so that an encrypted connection can be established between a web browser and a server.
When connecting to a site which uses HTTPS the data inside the packets is encrypted, this means that even if you are connected to an open Wi-Fi hotspot then any packets which are sniffed out of the air can’t be read.
However the problem is this, not all websites use HTTPS. Most of the popular sites will use HTTPS for sign-in, when you need to enter your username and password, and also for any financial transactions. But the rest of your visits to the site remain in the clear, open and exposed. Google has a good list of which sites fully utilize HTTPS and which ones don’t. Thanks to initiatives like Let’s Encrypt, the number of sites using HTTPS is growing rapidly.
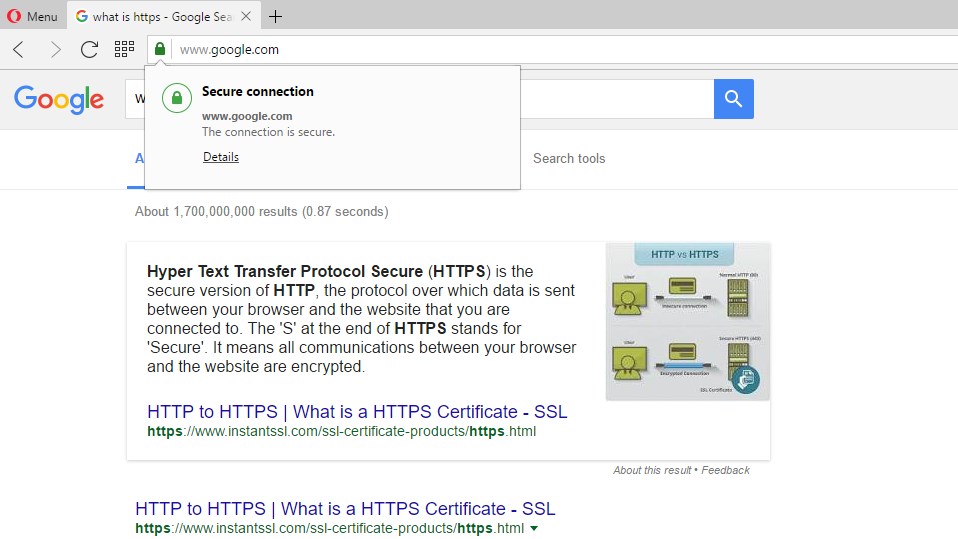
It is fairly simple with a web browser to see if a site is using encryption, however it is much harder with apps. On your browser you have various signs, like the padlock icon, which tell you that you are connecting to a secure website. But when you use an app, how can you be sure that it is safe? The short answer is that you can’t. Does your favorite app use encryption when it is posting your status updates to your friends? Is encryption used when you send a private instant message to someone? Is it safe to use a public Wi-Fi hotspot and then use third-party apps on your smartphone?
There are way to many apps to make a judgement call, but my initial reaction is no, it isn’t safe. That isn’t to say that there aren’t safe apps. For example, WhatsApp encrypts all forms of communication within the app but Google’s Allo only uses encryption in “incognito mode” and the search giant will store all non-incognito chats on its servers. Sounds to me like an Allo chats sent over an open Wi-Fi connection are ripe for the picking, but I haven’t tested it to see.
Capturing unencrypted packets out of the air isn’t the only way that public Wi-Fi can be dangerous. Whenever you connect to an open Wi-Fi router you are explicitly trusting the provider of that Wi-Fi connection. Most of the time that trust is well placed, I am sure the people running your local coffee shop aren’t trying to steal your personal data. However the ease with which we connect to open Wi-Fi routers means that hackers can easily setup a fake Wi-Fi hotspot to lure you into their traps.
Once a rogue hotspot has been established then all the data flowing through that hotspot can be manipulated. The best form of manipulation is to redirect your traffic to another site which is a clone of a popular site, however it is fake. The single aim of the site is to capture personal information. It is the same technique used in phishing email attacks.
What is more freighting is that hackers don’t need a fake hotspot to manipulate your traffic. Every Ethernet and Wi-Fi network interface has a unique address called a MAC address (where MAC stands for Media Access Control). It is basically used to make sure that the packets physically arrive at the right destination. The way devices, including routers, discover the MAC addresses of other devices is to use ARP, the Address Resolution Protocol. Basically your Android smartphone sends out a request asking which device on the network uses a certain IP address. The owner replies with its MAC address so that the packets can be physically routed to it.
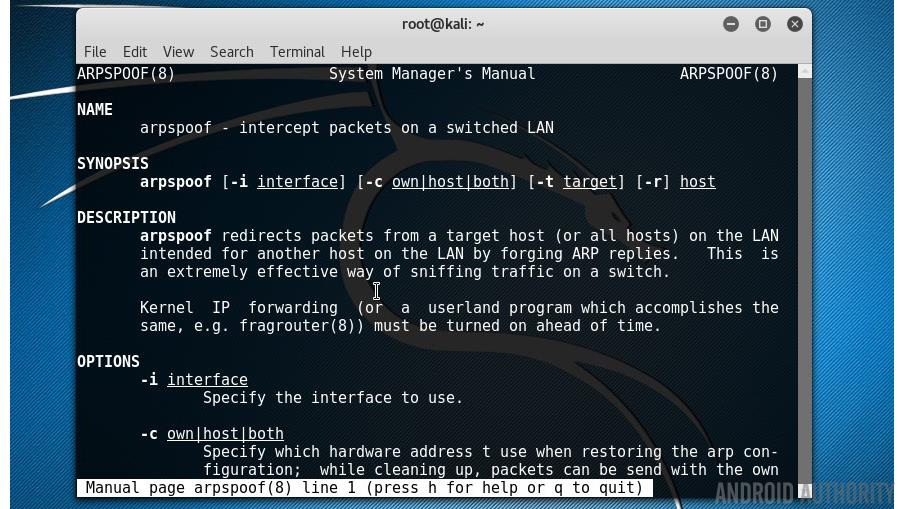
The problem with ARP is that it can be spoofed. That means that your Android device will ask about a certain address, say the address of the Wi-Fi router, and another device will reply with a lie, a fake address. In a Wi-Fi environment as long as the signal from the fake device is stronger than the signal from the real device then your Android smartphone will be deceived. There is a neat tool for this called arpspoof that comes with Kali Linux.
Once the spoofing has been enabled, the client device will send all the data to the fake router rather than to the real router, from here the fake router can manipulate the traffic however it sees fit. In the most simple case the packets will be captured and then forwarded on to the real router, but with the return address of the fake access point so that it can catch the replies as well!
With the growing use of HTTPS and secure connections using TLS, the ease at which data can be stolen has lessened, however with a laptop, a free Linux distro and an inexpensive Wi-Fi adapter you would be amazed at what you can achieve!
Do you think we should be more or less concerned about the encryption being used in our devices and how our communications are protected over the Internet? Please let me know below.
How easy is it to capture data on public free Wi-Fi? – Gary explains
Features
by Gary SimsFebruary 14, 2018
If you have read my article on what is a VPN? or read my review of Express VPN, you will have noticed that I recommend a level of caution when connecting to free public Wi-Fi hotspots. The reason is that all the traffic that goes from your device to the Wi-Fi router is unencrypted and because it is unencrypted then anyone who is within range of the same Wi-Fi signal can look at your Internet traffic! So, here is the question, just how easy is it to steal data on public free Wi-Fi?
There are three main problems with unencrypted public Wi-Fi hotspots. First, as I have mentioned, the packets of data that go from your device to the router are public and open for anyone to read. That sounds scary and it is, but thankfully because of tech like SSL/TLS it isn’t as bad as it was a few years ago.
Editor's Pick
What to do if your phone won’t connect to Wi-Fi
Second, hackers can quickly create fake rogue Wi-Fi hotspots, setup just to steal your info. Have you ever said to yourself, “Great! The coffee shop now has free Wi-Fi, it didn’t last week, they must have upgraded.” Did the coffee shop upgrade? Or is it some hacker just setting up a honey pot to catch you unawares?
Third, public Wi-Fi hotspots can be manipulate to launch man-in-the-middle (MitM) attacks where someone alters key parts of the network traffic or redirects your traffic to the wrong place. You might think you are connecting to Amazon.com but actually you are connecting to the hackers fake server designed just to capture your username and password.
Snooping and Sniffing

When you want to read a page on a website then your device will make a connection to the webserver to ask for the web page. It does that using a protocol called the HyperText Transfer Protocol (HTTP). On an open Wi-Fi router these requests and the responses can be seen by anyone who is listening. With wired networking then listening to the data packets zipping back and forth is more intrusive. However with wireless networking all that data is sent whizzing through the air, in every direction, for any Wi-Fi equipment to receive!
Normally a Wi-Fi adapter is set into “managed” mode which means it just acts as a client and connects to a single Wi-Fi router for access to the Internet. However, some Wi-Fi adapters can be set into other modes. For example, if I was configuring an access point (a hotspot) then the Wi-Fi needs to be set into “master” mode, more about that soon. Another mode is “monitor” mode. In “managed” mode a Wi-Fi network interface ignores all data packets except those specifically addressed to it. However in “monitor” mode the Wi-Fi adapter will capture all the wireless network traffic (on a certain Wi-Fi channel) regardless of the destination. In fact, in “monitor” mode the Wi-fi interface can capture packets without even being connected to any access point (router), it is a free agent, sniffing and snooping at all the data in the air!
Not all off-the-shelf Wi-Fi adapters can do this as it is cheaper for the manufacturers to make Wi-Fi chipsets that only handle “managed” mode, however there are some out there that can be placed into “monitor” mode. During my testing and research for this article I used the TP-Link TL-WN722N.
The easiest way to sniff Wi-Fi packets is to use a Linux distribution called Kali. You can also use the more standard distributions like Ubuntu, but you will need to install some of the tools yourself. If you don’t have Linux on a laptop then the good news is that Kali Linux can be used on a virtual machine like Virtual Box.
To capture the traffic we are going to use the aircrack-ng suite of tools, plus some others like driftnet, Wireshark and urlsnarf. There are plenty of tutorials out there about capturing traffic with aircrack-ng but here is the essence:
First you need to find out the name of your wireless network adapter, it will probably be wlan0, but to check it run ifconfig and then to double check, run iwconfig:

Next put the card into “monitor” mode, as I mentioned before, not all adapters/cards support this, so you must make sure you are using a compatible adapter. The command is:
sqlSelect All
airmon-ng start wlan0

This will create a new virtual interface called wlan0mon (or maybe mon0). You can see it using the iwconfig:

Wi-Fi uses radio and like any radio it needs to be set to a certain frequency. Wi-Fi uses 2.4GHz and 5GHz (depending on which variation you are using). The 2.4GHz range is split into a number of “channels” which are 5MHz apart. To get two channels which don’t overlap at all they need to be spaced around 22MHz apart (but that also depends on which variation of the Wi-Fi standard is being used). That is why channels 1, 6 and 11 are the most common channels as they are far enough apart so that they don’t overlap.
To capture data via a Wi-Fi adapter in “monitor” mode you need to tell the adapter which frequency to tune into, i.e. which channel to use. To see which channels are in use around you and which channel is being used by the free public Wi-Fi service you wish to test then use the airodump-ng command:
Select All
airodump-ng wlan0mon

The first list shows the Wi-Fi networks within reach of your laptop. The “CH” tells you which channel number each network is using (11, 6, 1 and 11) and the “ESSID” shows the names of the networks (i.e. the service set identifiers). The “ENC” column reveals if the network is using encryption and if so, what type of encryption. You can see from the screenshot that one of the networks is listed as OPN (i.e. OPEN). This is an open Wi-Fi access point I have setup in my house for testing purposes.
If the free Wi-Fi is on channel 6 then you now use the airodump-ng command to capture the data like this:
Select All
airodump-ng -c 6 -w allthedata wlan0mon

This will start capturing all the data on channel 6 and write it to a file called allthedata-01.cap. Let that run for however long you need and the press CTRL-C to exit.
OK, now we have a big lump of network traffic. The next step is to analyze that data. Network traffic contains lots of different information. For example there are all the broadcast packets which contain the information about the wireless network, the SSID etc. That is what your device receives when it is looking for the available networks. The question is, how can we sort through all the packets and find something interesting.
Each service on the Internet uses what is called a port, this is a way for a service (like a web server) and a client to communicate. Web servers use port 80, Email servers use port 25 (and some others), FTP uses port 21, SSH uses port 22 and so on. A single server can run multiple services (web, email, FTP, etc.) even though the IP address is the same, because each service uses a different port.
What this means is that I can sort the packets by port. I can filter out and examine the traffic working off port 80, i.e all web traffic. Or all the email traffic or whatever. It is also possible to dive deeper into the HTTP traffic and see what kind of data is coming back, images, javascript, whatever.
There are lots of different tools that you can use to filter the data in the network capture. Some simple command line tools include urlsnarf, dsniff and driftnet.
To filter out all the URLs from the data capture use:
Select All
urlsnarf -p allthedata-01.cap

To see if there are any passwords lurking around in the data then use:
Select All
dsniff -p allthedata-01.cap

And to see what pictures where being viewed use the driftnet tool:
Select All
driftnet -f allthedata-01.cap -a -d capturedimages

The -a option tells driftnet to write the images to disk rather than display them on screen. The -d option specifies the output directory.
If you don’t like the command line you can use Wireshark. This graphical tool allows you to look at each packet of data individually but it also offers lots of neat filtering. So if you type “http” into the filter bar then only the web related fields will be displayed. There is also the option to export all the images from the HTTP traffic via the File->Export Objects->HTTP menu item.

SSL/TLS and Android
If this was the end of the story then we would be in a very bad place. Any time you connect to an open Wi-Fi router then you are completely exposed. Thankfully there is help at hand in the form of SSL/TLS. Along side HTTP we have HTTPS, where the extra “S” on the end means secure, i.e. an encrypted connection. In the past HTTPS used SSL (Secure Sockets Layer) but that has now been replaced by TLS (Transport Layer Security). However since TLS 1.0 used SSL 3.0 as its basis then you often find that the two terms are used interchangeably. What TLS and SSL do is provide the protocol so that an encrypted connection can be established between a web browser and a server.
When connecting to a site which uses HTTPS the data inside the packets is encrypted, this means that even if you are connected to an open Wi-Fi hotspot then any packets which are sniffed out of the air can’t be read.
However the problem is this, not all websites use HTTPS. Most of the popular sites will use HTTPS for sign-in, when you need to enter your username and password, and also for any financial transactions. But the rest of your visits to the site remain in the clear, open and exposed. Google has a good list of which sites fully utilize HTTPS and which ones don’t. Thanks to initiatives like Let’s Encrypt, the number of sites using HTTPS is growing rapidly.

It is fairly simple with a web browser to see if a site is using encryption, however it is much harder with apps. On your browser you have various signs, like the padlock icon, which tell you that you are connecting to a secure website. But when you use an app, how can you be sure that it is safe? The short answer is that you can’t. Does your favorite app use encryption when it is posting your status updates to your friends? Is encryption used when you send a private instant message to someone? Is it safe to use a public Wi-Fi hotspot and then use third-party apps on your smartphone?
There are way to many apps to make a judgement call, but my initial reaction is no, it isn’t safe. That isn’t to say that there aren’t safe apps. For example, WhatsApp encrypts all forms of communication within the app but Google’s Allo only uses encryption in “incognito mode” and the search giant will store all non-incognito chats on its servers. Sounds to me like an Allo chats sent over an open Wi-Fi connection are ripe for the picking, but I haven’t tested it to see.
Rogue hotspots and man-in-the-middle attacks
Capturing unencrypted packets out of the air isn’t the only way that public Wi-Fi can be dangerous. Whenever you connect to an open Wi-Fi router you are explicitly trusting the provider of that Wi-Fi connection. Most of the time that trust is well placed, I am sure the people running your local coffee shop aren’t trying to steal your personal data. However the ease with which we connect to open Wi-Fi routers means that hackers can easily setup a fake Wi-Fi hotspot to lure you into their traps.
Once a rogue hotspot has been established then all the data flowing through that hotspot can be manipulated. The best form of manipulation is to redirect your traffic to another site which is a clone of a popular site, however it is fake. The single aim of the site is to capture personal information. It is the same technique used in phishing email attacks.
What is more freighting is that hackers don’t need a fake hotspot to manipulate your traffic. Every Ethernet and Wi-Fi network interface has a unique address called a MAC address (where MAC stands for Media Access Control). It is basically used to make sure that the packets physically arrive at the right destination. The way devices, including routers, discover the MAC addresses of other devices is to use ARP, the Address Resolution Protocol. Basically your Android smartphone sends out a request asking which device on the network uses a certain IP address. The owner replies with its MAC address so that the packets can be physically routed to it.

The problem with ARP is that it can be spoofed. That means that your Android device will ask about a certain address, say the address of the Wi-Fi router, and another device will reply with a lie, a fake address. In a Wi-Fi environment as long as the signal from the fake device is stronger than the signal from the real device then your Android smartphone will be deceived. There is a neat tool for this called arpspoof that comes with Kali Linux.
Once the spoofing has been enabled, the client device will send all the data to the fake router rather than to the real router, from here the fake router can manipulate the traffic however it sees fit. In the most simple case the packets will be captured and then forwarded on to the real router, but with the return address of the fake access point so that it can catch the replies as well!
Wrap-up
With the growing use of HTTPS and secure connections using TLS, the ease at which data can be stolen has lessened, however with a laptop, a free Linux distro and an inexpensive Wi-Fi adapter you would be amazed at what you can achieve!
Do you think we should be more or less concerned about the encryption being used in our devices and how our communications are protected over the Internet? Please let me know below.
 Similar topics
Similar topics» Send fast and easy and free emails via your gmail account using swift!
» Hackers can use python's pip to steal your data
» using apis audio capture and more
» Capture & Decode VOIP Calls With Wireshark
» Pen-testing Guide PCI Data Security Standard PCI DSS
» Hackers can use python's pip to steal your data
» using apis audio capture and more
» Capture & Decode VOIP Calls With Wireshark
» Pen-testing Guide PCI Data Security Standard PCI DSS
Page 1 of 1
Permissions in this forum:
You cannot reply to topics in this forum